As program director of TMC’s forthcoming SecureIT: Protecting Your Enterprise in a BYOD World, to be held in New York City on July 23, based on my inbox this week alone it is clear that this has become one of the most important topics on people’s minds. The headlines rightfully trumpet the news about cyber attacks and the latest data breach, but the truth is we are living through a transformation in thinking about overall risk management, which BYOD has helped drive.
And while not in the headlines all the time, the intensity of discussion and interest is already at a fevered pitch. In fact, there was so much on the subject this past week, it seemed useful to summarize some of the developments.
In no particular order here, they just a sample for what is going on.
Oracle announced the release of Oracle Communications Converged Application Server 5.1, a carrier-grade, standards-based development and deployment platform for next-generation communications services. The new release offers integrated support for Java, Web services and IP Multimedia Subsystem (IMS) standards, enabling communications service providers (CSP) to rapidly deploy voice, video and data services.
It is aimed squarely at servicing those BYOD devices and all of those third-party and home-grown apps.
Prestigous research firm ABIresearch released a report stating that BYOD and increased malware threats are helping drive growth in the mobile security industry. In this case, as you can see below, a picture is better than 1000 words.
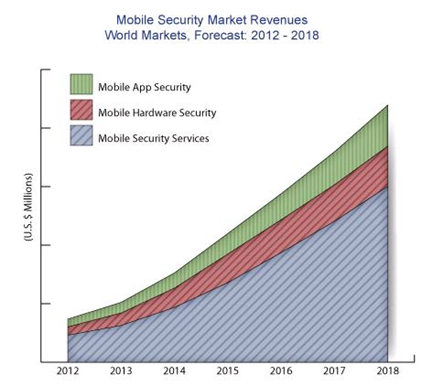
Source: ABIreseach
HP joined the fun with the announcement of HP Enterprise Cloud Services – Mobility, a cloud-based management solution that delivers secure anytime, anywhere access to applications and data from any mobile device.
According to HP, the new solution provides the fast and flexible deployment of tools and services for secure application access, file storage and sharing via multiple mobile platforms and all types of devices, including tablets and mobile phones. IT organizations are provided the tools to set appropriate security policies and the access controls to protect valuable corporate assets, applications and data.
The solution also allows users to download approved enterprise applications from a secure storefront, upload files to support collaboration and synchronize files between the HP cloud infrastructure and any mobile device. Mobile data is encrypted in transit and at rest, covering the device as well as the cloud infrastructure.
And, it provides the ability to configure cloud file storage that can scale up and down, offering local storage options that address data sovereignty and compliance requirements.
You also might wish to read the results of a recent an iGR survey, which found that 62 percent of U.S. SMBs have an official BYOD policy, and that over 73 percent of those surveyed said their company “unofficially” allows them to perform work-related activities on their personal devices.
This is not to mention a slew of webinars from various folks, on such interesting topics as: “Trust-basedApplication Control 101,” “Open your network to employee productivity—and close the door on threats,” and “The MDM Fallacy: One Size Does Not Fit All.” And, those are just the ones got in the past few days.
Reality is that we live in an age when BYOD has permanently changed the security paradigm of enterprises, and IT departments are aware that their control over security is slipping, as BYOD has fostered “shadow IT” operations by individuals, and lines of business cannot and will not wait for IT approval before taking things into their own hands – creating “IT Anarchy.”
The good news is the security industry is responding with solutions to help IT better manage the risks created by BYOD, and the need to manage people, devices, applications, content and network access. This is why the ABI numbers might actually be conservative. The not-so-good news is the bad guys are increasing the frequency and sophistication of their attacks, and surveys regarding IT readiness for managing risks along with user avoidance enterprise policies and rules (even in the face of known compliance issues) paints a less than rosy picture.
IT’s span of accountability is growing, while its actual control is being marginalized. To say there’s a lot at stake would be a gross understatement.
In the next few weeks, there are going to be a slew of announcements on everything relating to BYOD and security in the enterprise on the identity management, encryption, device management, applications and network management fronts, covering point solutions, cloud-based approaches, new authentication procedures and ways to provide better policy and context visibility and management. This will include some really interesting ones hitting on the need for companies to take a new and holistic approach to the shift BYOD has caused when it comes to risk management in general – and how all of this change will affect, to a significant degree, the way in which IT delivers security services and manages corporate risk in general.
We live in interesting times. In fact, because of the fluidity of the situation, the stakeholders in enterprise security are fully engaged in an interesting dialog about how to proceed given the chaos that currently exists. It’s a dialog that will be in full voice in New York on July 23, and we hope you’ll be part of the discussion. Hope to see you soon.
Edited by
Braden Becker