Intuitively, it makes sense to those who follow the online security issues that are popping up daily, that the Internet is an increasingly risky business place. In fact, for enterprise IT departments, the combination of the Bring Your Own Device (BYOD) phenomena that is picking up even more steam, along with the “virtualization” of work that relates to work being performed anywhere all the time - has conspired to alter the security paradigm forever and created a host of control (or lack thereof) challenges. Plus, we all know from personal experience what evil lurks in the form of phishing, other forms of identity theft and the misuse/abuse of our personal information.
Broomfield, CO-based Webroot, a provider of software-as-a-service (SaaS) Internet security for business and consumers and security intelligence solutions to organizations focused on cyber-security, has extraordinary visibility into security threats, particularly Web-borne ones. In fact, it recently expanded its partnership with Facebook so that its massive user based can protect themselves from anywhere by downloading the Webroot SecureAnywhere software for free. It also has been sharing its intelligence and insights on the state of threats in a two-part series of reports.
In Part 1 they looked at how Web-borne attacks were impacting businesses. They found the majority of them reporting significant effects in the form of increased help desk time, reduced employee productivity and disruption of business activities.
Part 2 is now available and it too is real food for thought. The report is based on a recent survey of organizations that currently have some type of Web security solution in place or are planning to deploy in the United States and the U.K. It was hosted by research firm Qualtrics with Lawless Research providing quantitative data analysis. It shows the impacts of Web-borne attacks are more severe for companies with employees who have remote access to the corporate network, or other corporate online resources, via their laptops, tablets or smartphones.
Disconcertingly, the research found that almost twice as many companies with remote users reported Web-borne attacks by cybercriminals which compromised the security of customer data and negatively impacted financials. In addition, as a result of BYOD and the virtual extinction of what were corporate perimeters, as more people access corporate resources remotely, the study says that compounding the situation is that most traditional security solutions are ineffective at stopping zero-day malware and companies do not give priority to implementing sensible policies and controls over remote users.
By the numbers
You are encouraged to download an read the entire report, but a few key findings need mention:
- 64 percent of companies allow remote access to servers for 25% to 100% of employees.
- 90 percent of companies agree that managing the security of remote users is extremely challenging.
- 71 percent of Web security professionals who say managing remote users is highly challenging experienced Web-borne phishing attacks in 2012.
- 50 percent of US firms with remote users estimate the cost of Web-borne attacks at $25,000 to $10 million.
What all of this highlights is the fact that enterprise IT departments along with, or because of, the behavior of their users, are losing or have lost control, and the associated risk management challenges are imposing. An example is that vulnerabilities in mobile Web browsers pose a major threat to mobile device security and have led to an increasing number of successful attacks according to survey respondents. Webroot notes that, “The device’s default browser and browsers embedded within apps are possible attack points, as mobile apps are increasingly reliant on Web browsers. Additionally, mobile device browsers often do not receive patches and updates, so while corporate systems can be manually configured not to trust compromised certificates or can receive a software patch in a matter of days, it can often take months to remediate the same threat on mobile devices.”
The new research points also points to data theft as the primary goal of attackers. This is not a shock since like bank robbers, the bad guys are going where the money is when they contemplate what to exploit. Mobile devices are a weak point because when compromised attackers can remotely run commands on the phone’s OS and malicious threats that use E-mail, SMS and a mobile Web browser to launch an attack, then silently record and steal data. The study found that companies with one-quarter or more of the their employees with remote access report higher rates of Web-borne attacks, with 50 percent experiencing Web site compromises in 2012.
As noted, a few of the charts in the study are illuminating. The two below provide some fascinating comparative data.
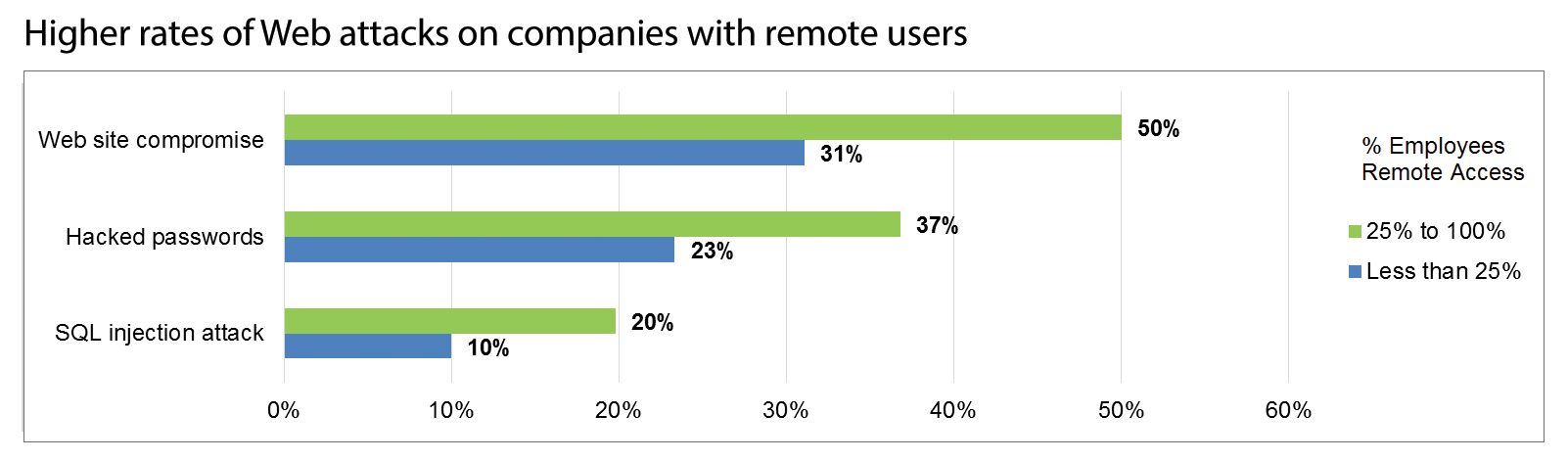
Source: Webroot
The above gets even more concerning as the chart below demonstrated as almost twice as many companies with a mobile workforce reported the Web-borne attacks compromised the security of customer data, negatively impacted financials and damaged the company’s reputation.
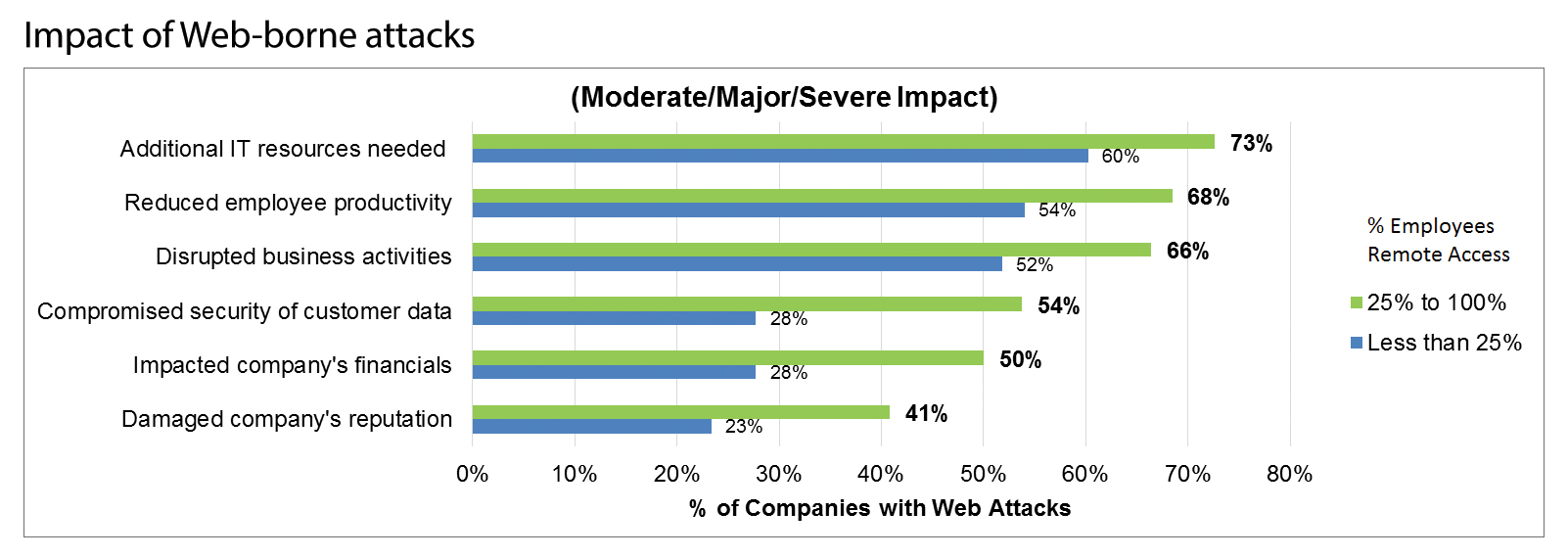
The research also showed that the cost of web attacks for companies with a larger percentage of remote workers is higher than those with fewer such employees working off premises. It found that:
- Half of U.S. companies with remote users estimate that Web-borne attacks cost $25,000 to $10 million in 2012, nearly double the rate of companies with less than 25 percent remote users.
- In the U.K., 43 percent of firms with remote users estimate the cost of attacks at £25,000 to £4 million, more than double the share of firms with less than a quarter of employees with remote access.
Protection suggestions concerning browser vulnerabilities
The study is not all doom and gloom. As Webroot correctly sees it, this is a case where the old bromide, “An ounce of prevention is worth a pound of cure,” is wisdom the masses and IT should follow.
Webroot advises companies to enforce a secure Web browser policy for all mobile device users. “This needs to be mandatory if employees are to have remote access to any corporate network, or other corporate online resources via their laptops, tablets or smartphones,” the company explains.
In fact, it provides the following advice on secure browser controls and components that will reduce the risks associated with mobile browsing. They are:
Integrate Browser-Based URL Filtering: Browser-based URL filtering technology stops users from accessing undesirable or malicious websites, including many that may host malware. With company owned devices it will also allow administrators to enforce compliance with acceptable Internet usage policies
Enforce Device-Level Security: A privacy or identity shield feature helps by isolating the browser from the rest of the device and stopping key loggers or other malicious software intercepting data about what a user is doing online. Passwords, authentication credentials and any other sensitive information are thus protected.
Perform Real-time Reputation Rating: For even safer browsing being able to perform real-time reputation scoring of search engine results from Google, Yahoo, Bing and Ask, and then identify those results as safe, unknown or known threats stops users clicking unintentionally through to malicious sites.
Deploy Anti-phishing Detection: Blocking phishing sites based on their characteristics, rather than immediately out of date blacklists is critical to stopping short-lived websites from stealing corporate or user data.
Establish Content Control Policies: To control browser content uploads and downloads is another important feature as often the posting of company documents to a personal email account or cloud storage service contravenes compliance rules and leads to undesirable data leakage.
Much of this is common sense. It is also heavily dependent on end user cooperation with IT, which other studies have shown is problematic. That said, the reality is that while managing the practices and behavior of remote workers is challenging, at least when it comes to Web-borne threats, there is much that can and should be done and what is a nominal price certainly far outweighs the risks of not implementing the propter protection.
Edited by
Stefania Viscusi