Let’s face it, if you are an IT professional you are probably painfully aware that we live in an age where much of your time is spent dealing with corporate governance requirements. You have the responsibility of creating, managing and enforcing policies and rules to mitigate risks and assure compliance.
The challenge you face is daunting.
- Can you authenticate users?
- Do you have visibility into what they have, what they are using, the applications and content they employ to do their jobs, etc.?
- Can you classify the unstructured data that needs to be accounted for to meet stringent governance requirements and provide that information securely and easily for audit purposes?
- Do you know the context of who, what, where, why, when and how, access to data is allowed and based on this can you take actions to assure the rules are being obeyed?
Yes, it is complicated. However, it is not impossible to get your arms around the above.
In fact, for IT professionals struggling with governance issues, Dell Software’s new Dell Quest One Identity Manager - Data Governance Edition Classification Module, is something to consider. This comprehensive solution has added identity to the classification of unstructured data. As Dell notes, “While other solutions simply classify data, Dell’s unique integrated solution discovers and classifies all new and old unstructured data, and goes beyond the data to show who has access and how it was obtained, to improve regulatory compliance and business agility.”
The problem with the explosion of unstructured data and associated risk
It is no secret that the amount of unstructured data flowing into enterprises is exploding. As a result there is a crucial need for those responsible for audits, risk and compliance to be able to categorize that data and the risks associated with exposure. And, it is not just about automating the task of data classification. Data is constantly being accessed, altered and on the move meaning IT needs to know what is going on and be capable of action to mitigate the possibility of it being compromised.
A survey conducted by Dell Software highlights the challenges:
- 52 percent of respondents have experienced at least 25 percent year-over-year growth in unstructured data across their organizations
- 63 percent stated that less than 25 percent of their organization’s data is currently classified as confidential and protected with additional security policies
- 45 percent are not confident in the security of their organization’s classified unstructured data
In summary, critical data is unprotected. As Dell Software points out protection starts with user access.
A look under the hood of Quest One Identity Manager and the Data Governance Edition
The new enhanced solution set provides context around users. It shows what they have access to in terms of entitlements to applications, roles within the company, and even geographical location. The integrated Classification Module adds the ability to discover and classify unstructured data contained in files and add context to that data. As Dell notes, the solution also boosts compliance. It is designed to ensure that only the right person has access to the data. Most importantly, should a security breach occur, or following an audit, accurate forensic information can quickly be obtained, showing exactly what the user had access to, whether any of that data was classified, who approved the access, and the last time access entitlement was reviewed.
Quest One Identity Manager - Data Governance Edition Classification Module integrates the new Classification Module with identity and data governance to provide the following new features:
MRI scan of the data - Finds, identifies and classifies unstructured data, and produces a Management Risk Index (MRI) report showing a heat map of the organization’s infrastructure, pinpointing the location of hot spots of unstructured data that contain the most risk.
Data classification risk levels - Assigns risk levels to data based on classification, providing clarity and enabling the business owner to see the level of risk for both the user and the data resource to which they are requesting access.
RapidView Summary - Finds, categorizes and organizes sensitive data such as credit card numbers and PII, based on content and context of access risk. Shows what kind of sensitive information is contained in unstructured data files without the need to manually evaluate them.
SecureTag for Eyes Only - Allows sensitive, unstructured data throughout the organization to be tagged according to compliance regulations, use, sensitivity, etc. The organization then can establish and enforce rules for how all existing and newly created sensitive unstructured data is treated, who may access it, and where it is stored.
Location-based tracking - Helps ensure the organization is meeting compliance requirements for any country in which the data is located. Data can be classified across the globe. In the event of a breach, the business owner can see where the data is located, who has access to it, and the classification level of the data set.
The graphic below provides a useful view of how all of this fits together.
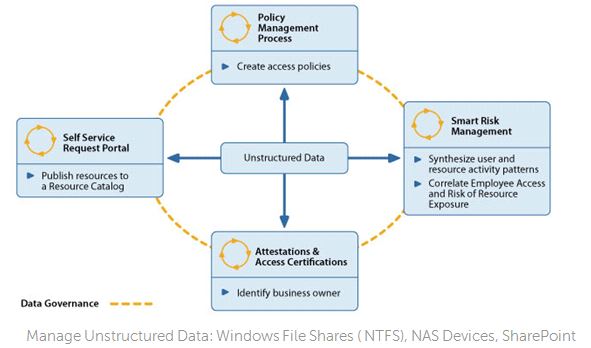
Source: Dell Software
And, the visibility fits what IT professionals say they are looking for. The screen shot below shows the accessible areas of statistical analysis and an overview of the high risks. The granularity of information behind this is deep.
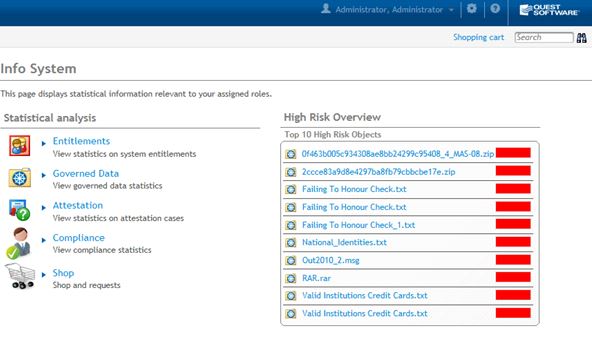
Source: Dell Software
John Milburn, executive director, Identity and Access Management Solutions, Dell Software stated that: “Our solution’s unique capability to add identity to unstructured data can improve security, compliance and business agility. Business owners can better manage data assets when they know what’s in the data itself, and can assign a risk level for each user, depending on what other permissions the user has. The Quest One Identity Manager - Data Governance Edition Classification Module gives business owners insight into both the data, and the roles and responsibilities of users, so they can make informed decisions on access requests to help further reduce the organization’s exposure to risk.”
In speaking with Jonathan Sander, Director, Product Strategy, Dell Software, he observed that, “This is about creating a new level of business intelligence based on Dell’s commitment to being connected at the product level.” He added that, “We are providing three things critical in risk mitigation: visibility, classification and context. We have put everything in one place so policies and rules can be created and enforced with a level of detail that goes to the heart of compliance assurance. IT now has the tools to organize, synthesize and analyze everything related to governance with focus on unstructured data. They also can give access, attest and certify, make risks apparent and incorporate all of this into policy.”
As noted at the top this is a comprehensive solution. The content of files can be known, unstructured data automatically rather than manually classified and tagged, and using the full knowledge of context is brought back into the identity platform. As Sander concluded, “This is connected to reality of their infrastructure.”
Martin Kuppinger, founder and principal analyst, KuppingerCole, agreed the solution, “Incorporates easy-to-use capabilities for access request management, strong role management, and other standard access governance using unique characteristics that include the ability to roll back collected audit data to earlier points in time.”
Quest One Identity Manager - Data Governance Edition Classification Module is generally available on June 10 for $35USD per enabled user. Though the Classification Module requires the purchase of Quest One Identity Manager - Data Governance Edition to function, the module can be purchased separately by those who already own Quest One Identity Manager - Data Governance Edition.
Visibility, classification and context all controlled through a single dashboard and with a lot of critical functionality. A window on your world you may wish to open.
Edited by
Stefania Viscusi