The good folks at the Juniper Mobile Threat Center (MTC) are on the job 24/7/365, looking at and analyzing individual instances of mobile malware. Hence, they have an unusual catbird seat on what the bad guys are up to, and to put it mildly, “no good” is on the rise. In fact, the company is out with its third annual Mobile Threats Report, which looks at attacker activity from March 2012 to March 2013, and it is really getting ugly out there. It is based on analysis of more than 1.85 million mobile applications and vulnerabilities, up more than 133 percent from the last report released in February 2012.
The headline findings alone are enough to give all of us pause:
- The bad actors are busy turning mobile malware into a profitable business. In fact, it is clear malware writers are increasingly behaving like profit-motivated businesses.
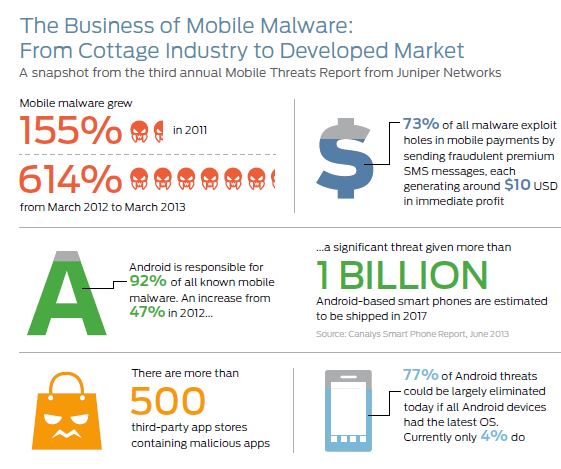
- Mobile malware threats are growing at a rapid rate of 614 percent to 276,259 total malicious apps, demonstrating an exponentially higher cyber criminal interest in exploiting mobile devices.
It gets even more nightmarish, especially if you are the owner of an Android device. Like bank robbers who go where the money is, because of the increasing popularity of Android (67.7 global market share according to analyst firm Canalys), 92 percent of all MTC detected threats were aimed at devices running Android devices. To make matters worse, attackers are leveraging loosely regulated third-party app marketplaces to distribute malware and more quickly get threats on the market.
The devils are in the MTC report details
The MTC report uncovered several mobile malware trends that demonstrate increased business savvy by attackers including:
- Preying on High-Growth Market Opportunities: Mobile malware developers are recognizing huge opportunity in the growing market dominance of Android. Malware for the Android operating system has increased at a staggering rate since 2010, growing from 24 percent of all mobile malware that year to 92 percent by March 2013.
- More Effective Distribution: Attackers made strides to shorten the supply chain and find more agile methods to distribute their wares into the wild around the globe. The MTC identified more than 500 third-party Android application stores worldwide, most with very low levels of accountability or oversight, that are known to be hosting mobile malware – preying on unsuspecting mobile users as well as those with jail-broken iOS mobile devices. Of the malicious third-party stores identified by the MTC, three out of five originate from either China or Russia.
- Multiple Paths to Big Profits: Almost three-fourths (73 percent) of all known malware are FakeInstallers or SMS Trojans, which exploit holes in mobile payments to make a quick and easy profit. These threats trick people into sending SMS messages to premium-rate numbers set up by attackers. Based on research by the MTC, each successful attack instance can yield approximately $10 in immediate profit. The MTC also found that more sophisticated attackers are developing intricate botnets and targeted attacks capable of disrupting and accessing high-value data on corporate networks.
- Exploiting Industry Fragmentation: The fragmented Android ecosystem keeps the vast majority of devices from receiving new security measures provided by Google, which could leave users exposed to even known threats. According to Google, as of June 3, 2013, only 4 percent of Android phone users were running the latest version of the operating system, which provides mitigation against the most popular class of malware measured by the MTC that makes up 77 percent of Android threats.
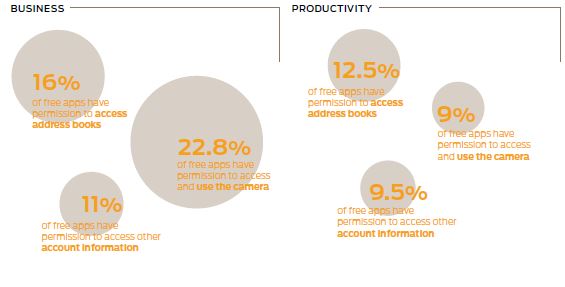
- Increasing Privacy Violations: In addition to malicious apps, Juniper Networks found several legitimate free applications that could pose a risk of leaking corporate data on devices. Juniper Networks found free mobile applications sampled by the MTC are three times more likely to track location and 2.5 times more likely to access user address books than their paid counterparts. Free applications requesting/gaining access to account information nearly doubled from 5.9 percent in October 2012 to 10.5 percent in May 2013.
One graphic from the report unfortunately paints the stark realities of bad actors increasing the frequency, sophistication and expanded reach of their attacks.
Click on image to enlarge
Source: Juniper Networks Third Annual Mobile Threats Report
In commenting on the report, Michael Callahan, vice president of global product marketing for the Security Business, Juniper Networks, stated, “With mobile malware on the rise and attackers becoming increasingly clever, we need better protection for mobile users and corporations. While on one hand the OEMs, carriers and software vendors must collaborate to develop platforms that mitigate large threats, enterprises and government organizations need to take a comprehensive look at protecting their data and networks by adopting a holistic approach to mobile security.”
Troy Vennon, director of the Mobile Threat Center, Juniper Networks, noted: “There’s no doubt mobility will continue to be a pervasive and disruptive force across every industry. We have found that it has created an easy business opportunity for malware developers who are becoming savvy in their approach to quickly turn profits in a rapidly growing market. We anticipate that similar to the evolution of PC-based threats, mobile attacks will continue to increase and become more sophisticated in the coming years.”
TechZone360 had an opportunity to discuss the report with Vennon, and he had several cogent observations about the findings. First, Vennon said, “There is a perfect storm creating opportunities for those with malicious intent to profit from the increasingly rich number of targets.” He explained that “the combination of explosive device growth, the availability of malware infected apps from third-party app stores, and industry fragmentation, notably in the Android ecosystem where Google has done a good job of providing defense against attackers but where roughly only 4 percent of users are running the latest version of Android which has protections, invites attacks.”
Reality is the attacks can be simple but lethal. The two most common are SMS Trojans and Fake Installers. The trojans infect what seem to be normal apps with the ability to send SMS text messages to premium services where charges are then automatically applied to an unsuspecting user’s mobile bill. Fake installers as the name implies accomplish basically the same feat.
“Android is the perfect target,” Vennon continued. “Not only is it increasing in market share, but it has an open development environment and the fragmentation of the industry where updates to the OS are not pushed out by service providers or device manufactures is why so few people are current in their protection.”
Vennon also noted that there are over 500 third-party app stores hosting mobile malware, and their enticements are beguiling. “Russia and China account for three out of five of the places hosting mobile malware,” he explained. “In addition, given the average attack can net about $10, the incentive to continue to exploit the low hanging fruit is irresistible. It really pays. There is little or no review of the apps in these stores and the shelf-life of the apps is long.”
The entire report is worth a good read. A big reason is because of findings that, as a result of BYOD’s growing presence in enterprises, the bad guys are now turning their attention to compromising high-value data on corporate networks and devices. Indeed, it notes that current e-mail “NotCompatible” attacks on an unprotected device could allow an attacker access to the organizations internal network. The report even provides a section on precisely how “NotCompatible” works.
Another graphic highlights the issue. Free apps come with consequences.
Click on image to enlarge
Source: Juniper Networks Third Annual Mobile Threats Report
Finally, the report has a series of recommendation as to how to better secure your environment based on a holistic approach. These include:
- Securing connectivity – implementing mobile VPNs with strong identity-based authentication, and exploring the use of application-level VPN.
- Control the attack surface – implement secure access systems that provide network-level mobile security; consider adherence to internal and regulatory compliance requirements, utilize mobile device management features that blacklist bad apps; and manage what users can download.
- Protect against malware – enable mobile anti-virus subscriptions, and ensure mobile device management and control.
As Vennon stated, “A holistic approach is necessary, the industry needs to do a better job to decrease fragmentation, and focus must be paid on really securing the endpoints.” The solutions are out there and, as the report shows, the urgency for implementing them is high.
Edited by
Alisen Downey