It is getting hard to keep up with breaking news these days in general, but even harder to stay on top of all of the online outages (Amazon, Google and Microsoft in just the past few days), data breaches and hack attacks. And this is without mentioning all the NSA scandal and ripple effect news.
Thus, the fact that an Islamist cyber terrorist calling him or herself the “Mauritania Attacker” is out boasting to Indian security website Techworm of having hacked Twitter today, and has leaked account credentials (not passwords) of over 15,000 users, is not surprising – even though it is obviously disturbing. In fact, if you would like to see if your account was part of the “oauth_token secret codes” dump by this individual, check out Pastebin.com.
What we know now
Here is what we know at the moment. Mauritania Attacker may be overstating the fact that he or she can get into the entire user database on Twitter and that no account is safe, but thus far the evidence is rather compelling that the hacker can cause some serious mischief. The reason is that OAuth2 goes directly to the increasing use of social media login information to access other apps. In other words, bad stuff can travel fast, and security experts are advising that all of us tweeters would be smart to revoke and re-establish access to connected third-party apps. In two words, “Darn it!”
The U.K.-based website The Register has a rather thorough story about the niceties of all of this replete with some colorful language by author John Leyden that is wonderfully British— “twit” and “miscreant” are two of my favorite words you don’t see often in tech articles. As Leyden notes, problems with OAuth tokens being vulnerable are not new. In fact, researchers have pointed out one set of problems, which may or may not have been employed in this current attack, several weeks ago, and Twitter has not responded with suggestions as to how to mitigate the problems. One suspects, or at least hopes, they now will be more forthcoming.
Another case where a little transparency would be helpful
For those who have followed my coverage of the challenges online services of all types are having in reacting to what euphuistically I will call “service problems,” the common thread of the critique is a call for more transparency from the impacted vendor. Apologies are nice but it is like when your kids do something wrong and get caught and we tell them, “We know you are sorry, but what you seem to be most sorry about is getting caught, now change the behavior.”
Here is what we in the press encounter when going to the Twitter corporate press site:
If you click on the @Twitter link, here was the view at 2:30 p.m. EDT.
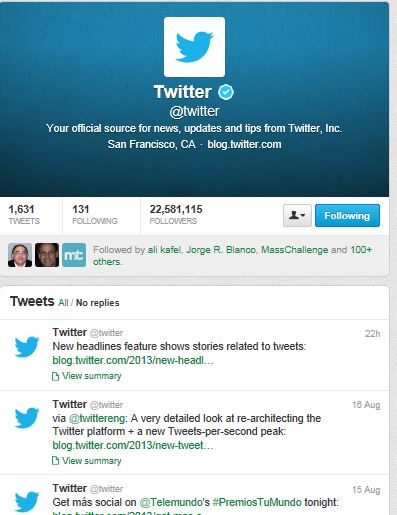
Yes. You are reading this correctly, with over 22 million followers there is ZERO news.
But wait, it gets even better. Here is the page view a few minutes later from @twittercomms.
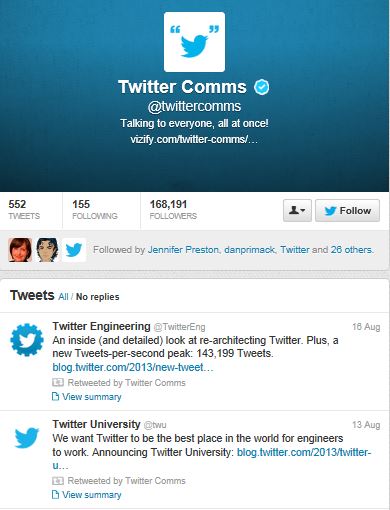
Again, your eyes are not deceiving you. The last posting about anything was on August 16.
Twitter has become in many ways the default for breaking news. Indeed, the breaking news about the gunfire heard at an Atlanta-area charter school that is unfolding as this is written is a great example, along with all of the traffic generated by things like the Boston Marathon bombing. It has also proven to be an invaluable tool for obtaining help, even when that term is broadly defined. This leads to two questions for Twitter:
- If the hacker can access our accounts, why didn’t Twitter send out an alert?
- Where is the advice on what to do regarding associations with third-party apps?
The sun has not yet set today, so it is too early to call this a true day of shame for Twitter. However, it is certainly shaping up to be one. As the refrain from the Peter Seeger’s folk music classic (made famous by Peter, Paul and Mary) “Where have all the flowers gone?” concludes, “Oh, when will they ever learn? Oh, when will they ever learn?”
Edited by
Alisen Downey