At the risk of being accused of being a bearer of bad tidings, the release of the “McAfee Threats Report: Second Quarter 2013” can do all of the explaining. The just issued report found that Android-based malware achieved a 35 percent growth rate not seen since early 2012.
As McAfee notes, “This rebound was marked by the continued proliferation of SMS-stealing banking malware, fraudulent dating and entertainment apps, weaponized legitimate apps and malicious apps posing as useful tools. McAfee Labs registered twice as many new ransomware samples in Q2 as in Q1, raising the 2013 ransomware count higher than the total found in all previous periods combined.” In a word, “YIKES!”
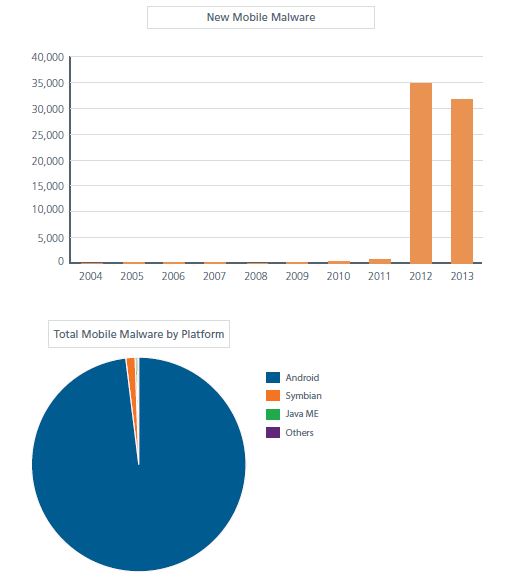
Source: McAfee Threats Report: Second Quarter 2013
The report also highlights that in virtually every aspect of malicious activity the last quarter saw the bad guys stepping up the pace. For example, there was a 16-percent increase in suspicious URLs and a 50-percent increase in digitally-signed malware samples. The report further sites notable events in the cyber-attack and espionage areas, including multiple attacks on the global Bitcoin infrastructure and revelations around the Operation Troy network targeting U.S. and South Korean military assets, all of which are explored in detail.
They did not mention a number of other prominent incidents that included attacks on various types of major retailers, media and social media sites, etc.
Returning to mobile challenges for a moment, McAfee Labs researchers identified a set of common mobile strategies employed by cybercriminals to extract money and confidential information from victims. As you can see from reading the descriptions below this is not just a true rogue’s gallery of nasty stuff, but hopefully it will serve as a bit of guidance for not be fooled yourself. Horrible mobile attacks include:
- Banking Malware. Many banks implementing two-factor authentication require customers to log into their online accounts using a username, password and a mobile transaction number (mTAN) sent to their mobile device via a text message. McAfee Labs researchers identified four significant pieces of mobile malware that capture the traditional usernames and passwords, and then intercept SMS messages containing bank account login credentials. The malicious parties then directly access accounts and transfer funds.
- Fraudulent Dating Apps. McAfee Labs discovered a surge in dating and entertainment apps that dupe users into signing up for paid services that do not exist. Lonely users attempt to access potential partners’ profiles and other content only to become further frustrated when the scam is recognized. The profits from the purchases are later supplemented by the ongoing theft and sale of user information and personal data stored on the devices.
- Trojanized Apps. Research revealed the increasing use of legitimate apps altered to act as spyware on users' devices. These threats collect a large amount of personal user information (contacts, call logs, SMS messages, location) and upload the data to the attacker’s server.
- Fake Tools. Cyber criminals are also using apps posing as helpful tools, such as app installers that actually install spyware that collects and forwards valuable personal data.
“The mobile cybercrime landscape is becoming more defined as cybergangs determine which tactics are most effective and profitable,” said Vincent Weafer, senior vice president of McAfee Labs. “As in other mature areas of cybercrime, the profit motive of hacking bank accounts has eclipsed the technical challenges of bypassing digital trust. Tactics such as the dating and entertainment app scams benefit from the lack of attention paid to such schemes; while others simply target the mobile paradigm’s most popular currency: personal user information.”
However, with over 147 million malware types now in what McAfee calls its “zoo,” the researchers were also quick to point out that while certain types of old favorites are declining in use in the non-mobile arena, the statistics unfortunately highlight what they call, “The continued adaptability of attackers in adjusting tactics to opportunities, challenges to infrastructure upon which commerce relies, and a creative combination of disruption, distraction and destruction to veil advanced targeted attacks.” These include:
- Ransomware. Over the past two quarters McAfee Labs has catalogued more ransomware samples than in all previous periods combined. The number of new samples in the second quarter was greater than 320,000, more than twice as many as the previous period, demonstrating the profitability of the tactic.
- Digitally-signed Malware. Malware signed with legitimate certificates increased 50 percent, to 1.2 million new samples, rebounding sharply from a decline in the first quarter. The trend of illegitimate code authenticated by legitimate certificate authorities could inevitably undermine confidence in the global certificate trust infrastructure.
- Suspicious URLs. The second quarter’s increase in suspicious URLs shows how important “infected” sites remain as a distribution mechanism for malware. At June’s end, the total number of suspect URLs tallied by McAfee Labs reached 74.7 million, which represents a 16-percent increase over the first quarter.
- Spam Volume. Global spam volume continued to surge through the second quarter with more than 5.5 trillion spam messages. This represented approximately 70 percent of global e-mail volume.
- Attacks on Bitcoin Infrastructure. The sudden activity in the Bitcoin market over the course of the past quarter attracted interest from cybercriminals. In addition to disruptive distributed denial of service attacks (DDoS), the group infected victims with malware that uses computer resources to mine and steal the virtual currency.
- Operation Troy. McAfee Labs uncovered evidence suggesting that attacks on South Korean banks and media companies in March and June of this year were in fact connected to an ongoing cyber espionage campaign dating back to 2009. A study of forensic evidence suggested that the campaign was designed to target U.S. and South Korean military systems, identify and remove confidential files, and, when necessary, destroy the compromised systems through a master boot record (MBR) attack. Read the full report: “Dissecting Operation Troy: Cyber Espionage in South Korea.”
The reason the McAfee report is one that commands so much attention stems from the extensive implementation of its security solutions around the world. They put a lot of resource (500 researchers in 30 countries) into tracking and analyzing threats which is another reason why downloading the report and looking at the graphics and explanations is time well spent. As noted at the top it is always difficult to be the messenger of less than wonderful news, but when it comes to security knowledge is power in terms of preparedness to identity, remediate and protect your valuable information assets whether you are an enterprise or as the report notes are an individual mobile user who increasingly is being targeted not just for “fun” but for profit.
And, while the industry is getting good at letting us know about all of the activities, the reports IT administrators look at, and that we can all get from looking at scanning results are the real tales of what is going on. It is how we keep score on how well our protection is holding up, and an indicator of both our vulnerability as well as where we might wish to be more proactive.
Edited by
Alisen Downey