All of the recent news regarding data breaches at major retailers has raised a series of questions that speak to the urgency of finding solutions as emboldened bad actors increase the sophistication and frequency of their cyber-attacks. Not the least of these questions is whether enterprises, particularly those who handle millions of customer records, have the threat intelligence they need to quickly respond to and resolve the growing undermining of trust which is the foundation of e-commerce’s vitality.
The issue of readiness, including visibility and remediation capabilities are the subjects of a new study by Linden, UT-based incident resolution solutions provider AccessData and the Ponemon Institute, which conducts independent research, educates leaders from the private and public sectors and verifies the privacy and data protection practices.
The report, Threat Intelligence & Incident Response: A Study of U.S. & EMEA Organizations, sponsored by AccessData, surveyed 1,083 CISOs and security technicians in the United States and EMEA about how their company handles the immediate aftermath of a cyber-attack and what would help their teams more successfully detect and remediate these events. It sought information about: the use of threat intelligence to defend against cyber attacks; the current state of incident response; IT professiona;ls understand of the importance of getting to the root cause is critical to stopping future attacks; and, what is going on in the critical areas of mobility and e-discovery.
Lack of preparedness and tools is “startling”
The term “sobering” is one I have used way too often is the coverage of security reports. While it applies to the findings in this one, the use of the term “startling” by the authors may be more appropriate. A few facts from the survey illustrate why.
When a CEO and Board of Directors asks a security team for a briefing immediately following an incident:
- 65 percent of respondents believe that the briefing would be purposefully modified, filtered or watered down.
- 78 percent believe most CISOs (Chief Information Security Officers) would make a “best effort guess” based on limited information, and they would also take action prematurely and report that the problem had been resolved without this actually being the case.
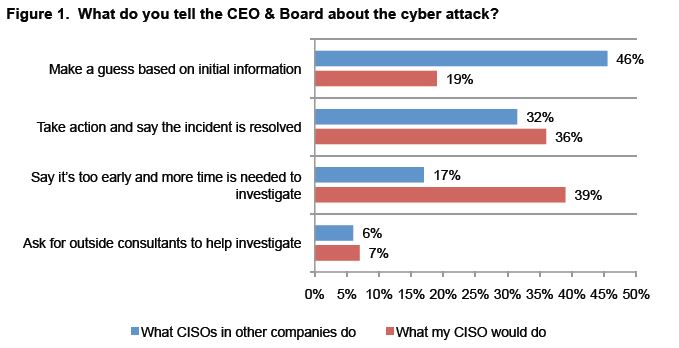
Source: Threat Intelligence & Incident Response: A Study of U.S. & EMEA Organizations
Some of the findings that highlight the lack of preparedness are almost jarring. For example:
- An average of 35 percent of all cyber attacks are undetected.
- 86 percent of respondents say detection of a cyber attack takes too long
- 85 percent say there is little or no prioritization of incidents.
- 40 percent say their security products do not support the import of threat intelligence from other sources.
- 55 percent do not believe their security team has sufficient skills to investigate and remediate a security incident.
- 38 percent say it could take a year to know the root cause of a cyber attack
- 41 percent say their organizations will never know with certainty the root cause.
- 86 percent rate the investigation of mobile devices as difficult.
- 59 percent say they are not able to conduct investigation on mobile devices in response to e-discovery requests or they are unsure.
- In the case of being able to locate sensitive data on mobile devices, 54 percent say they are not able to or are unsure.
In commenting on the findings, Dr. Larry Ponemon, chairman and founder of the Ponemon Institute stated: “When a cyber-attack happens, immediate reaction is needed in the minutes that follow, not hours or days…It’s readily clear from the survey that IR processes need to incorporate powerful, intuitive technology that helps teams act quickly, effectively and with key evidence so their companies’ and clients’ time, resources and money are not lost in the immediate aftermath of the event.”
There obviously is a lot to digest regarding all of the above. However a pullout that deserves attention in the one about importing and utilizing threat intelligence to augment the capabilities of existing security products which would give CISOs enhanced abilities to be not just reactive but proactive in dealing with cyber attacks. The graphic below highlights this.
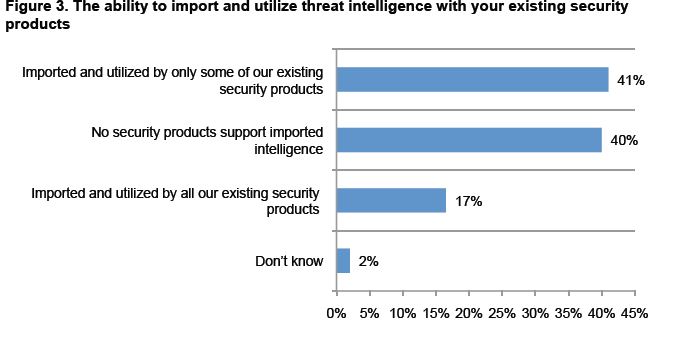
Source: Threat Intelligence & Incident Response: A Study of U.S. & EMEA Organizations
“Today, companies focus primarily on the protective aspect of their information security,” said Craig Carpenter, Chief Cybersecurity Strategist at AccessData. “While protection is obviously important, this research reinforces the critical need for organizations to invest in automated IR technology integrating security, forensics and eDiscovery solutions to facilitate not just incident response, but incident detection, investigation and resolution. CISOs are clearly saying their disparate tool sets are not keeping up with the threats they face. What they need is an incident resolution platform that doesn’t just integrate alerts from myriad point solutions, but makes intelligence actionable and automates significant portions of the IR process, allowing them to focus on the most pressing incidents.”
It may sound like a statement of the obvious, but CISOs are deeply aware (pardon the pun) that you can’t defend against what you don’t know. Visibility has always been important, but never more so than now. As the survey results show, unfortunately CISOs do not believe they have the visibility they need to discover and respond quickly to threats, or the skilled people required to turn what truly are actionable insights into enhanced protection. This is good news for cyber attackers and bad news for the rest of us.
The axiom that fore-warned is fore-armed resonates with CISOs. This report in that respect can be a valuable vehicle for CISOs to engage their management in discussions as to where advanced threat intelligence investments can have significant impact in risk mitigation. The headlines only amplify the sense of urgency in having that discussion.
Edited by
Cassandra Tucker