We know from the headlines that cyber attacks of all types have become more frequent and more sophisticated. It is also well known that those will malicious intent,whether they're organized criminals, state-sponsored terrorists or just bad actors looking to monetize an opportunity, are always looking for vulnerabilities to exploit, particularly in enterprises. Putting the constant news of a new exploit aside, it is always a good idea to turn to those tracking the who, what, where, why, when and how the bad guys are working.
In this regard, a trusted source for insights on the nature and extent of attacks is what is becoming an annual report from San Jose, California-based real-time cyber attack detection specialists Vectra Networks. They are out with the second edition of the company’s Post-Intrusion Report, a real-world study about threats that evade perimeter defenses and what attackers do once they get inside your network. It is both illuminating and disturbing.
The report data was collected over six-months from 40 customer and prospect networks with more than 250,000 hosts, and contains a comparison to results in last year’s report. The latest edition includes detections of all phases of a cyber attack and exposes trends in:
- Malware behavior
- Attacker communication techniques
- Internal reconnaissance
- Lateral movement
- Data exfiltration
The report is also the first to study hidden tunnels without decrypting SSL traffic by applying data science to network traffic. A comparison of hidden tunnels in encrypted traffic vs. clear traffic shows that HTTPS is favored over HTTP for hidden tunnels, indicating an attacker’s preference for encryption to hide their communications.
Report data is based on metadata from Vectra customers and prospects who opted to share detection metrics from their production networks. Vectra identifies active threats including the critical area of internal host-to-host traffic and traffic to and from the Internet to ensure visibility and context of all phases of an attack. This is how the information as to what happens once the bad guys can be detected and tracked.
Significantly, despite preventive measures taken by most companies at various levels, the report offers analysis of active “in situ” network threats that bypass next-generation firewalls, intrusion prevention systems, malware sandboxes, host-based security solutions, and other enterprise defenses. Results are from 40 organizations in education, energy, engineering, financial services, government, healthcare, legal, media, retail, services, and technology.
Views of intrusions to be aware of
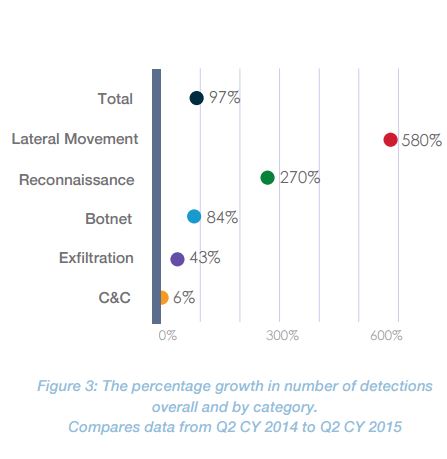
The bad news is that there was non-linear growth in lateral movement (580 percent) and reconnaissance (270 percent) detections that outpaced the 97 percent increase in overall detections compared to last year. As the report notes, “These behaviors are significant as they show signs of targeted attacks that have penetrated the security perimeter.”
A look at the types of activities tells the tale of what is going on.
As can be seen from the above:
- Lateral-movement detections, which track the internal spread of malware and authentication-based attacks such as the use of stolen passwords, led the pack with over 34 percent of total detections.
- Command and control detections, which identify a wide range of malicious communication techniques, were close behind with 32 percent of detections.
- Botnet monetization detections track the various ways criminals make money from ad click-fraud, spamming behavior, and distributed denial of service (DDoS) attacks. These botnet-related behaviors accounted for 18 percent of all detections.
- The reconnaissance category looks for internal reconnaissance performed by an attacker already inside the network and represented 13 percent of detections.
- Exfiltration detections look for the actual theft of data. The good news here is that it was by far the least common category of detection at 3 percent.
The growth rates in the categories are equally problematic.
“The increase in lateral movement and reconnaissance detections shows that attempts at pulling off targeted attacks continue to be on the rise,” said Oliver Tavakoli, Vectra Networks CTO. “The attackers’ batting average hasn’t changed much, but more at-bats invariably has translated into more hits.”
Other key findings of the study include:
- Botnet monetization behavior grew linearly compared to last year’s report. Ad click-fraud was the most commonly observed botnet monetization behavior, representing 85 percent of all botnet detections.
- Within the category of lateral movement detections, brute-force attacks accounted for 56 percent, automated replication accounted for 22 percent, and Kerberos-based attacks accounted for 16 percent. Although only the third most frequent detection, Kerberos-based attacks grew non-linearly by 400 percent compared to last year.
- Of Internal reconnaissance detections, port scans represented 53 percent while darknet scans represented 47 percent, which is fairly consistent with behavior detected last year.
 Image via Shutterstock
Image via Shutterstock
One of the things grabbing the news these days is the long time it takes for exploits to be detected. The challenge, given the ability of attackers to circumvent typical defenses is to do what Vectra Networks does which is use its on wire capabilities to monitor traffic anomalies behind perimeter defenses.
In discussing the findings with TechZone360, Vectra executives noted that applying data science at the packet live to live sessions is the key to detection and that finding the hidden communications tunnels is also critical. Realities are that you can’t defend against what you don’t see and know. The problem, as the study highlights and as Vectra explained is that, “the Kill Chain” is getting deeper and deeper into the network hence having the tools to be more vigilant and the analytics to be more proactive are critical.
Edited by
Dominick Sorrentino