TechZone360
Featured News
Last Updated: 6:20 AM EST - Apr 27, 2024ChatGPT Isn't Really AI: Here's Why
ChatGPT is the biggest talking point in the world of AI, but is it actually artificial intelligence? Click here to find out the truth behind ChatGPT.
Read MoreRevolutionizing Home Energy Management: The Partnership of Hub Controls and Four Square/TRE
Through a recently announced partnership with manufacturer Four Square/TRE, Hub Controls is set to redefine the landscape of home energy management in…
Read More4 Benefits of Time Tracking Software for Small Businesses
Time tracking is invaluable for every business's success. It ensures teams and time are well managed. While you can do manual time tracking, it's time…
Read MoreHow the Terraform Registry Helps DevOps Teams Increase Efficiency
A key component to HashiCorp's Terraform infrastructure-as-code (IaC) ecosystem, the Terraform Registry made it to the news in late 2023 when changes …
Read MoreNightmares, No More: New CanineAlert Device for Service Dogs Helps Reduce PTSD for Owners, Particularly Veterans
Canine Companions, a nonprofit organization that transforms the lives of veterans (and others) suffering PTSD with vigilant service dogs, has debuted …
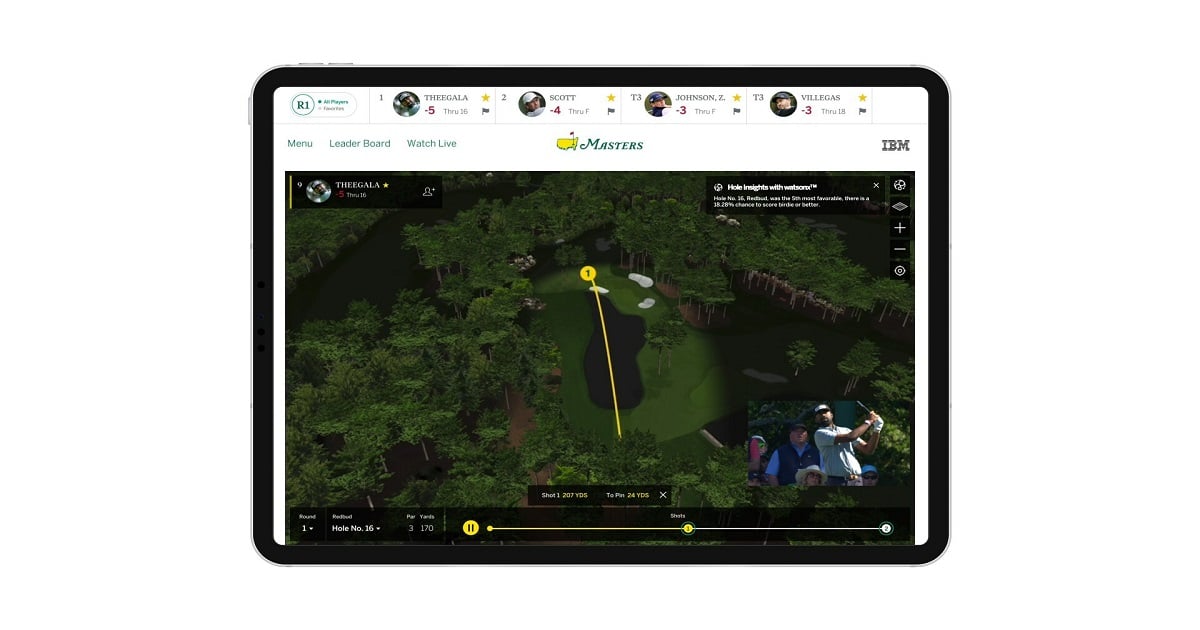
Read MoreIBM's AI Brings Data-Driven Insights and Spanish Narration to the Masters
The Masters Tournament and IBM announced new features for the 2024 Masters app and Masters.com, powered by watsonX.
Read MoreIN-DEPTH ANALYSIS & INTERVIEWS
Last Updated: Apr 27, 2024ChatGPT Isn't Really AI: Here's Why
ChatGPT is the biggest talking point in the world of AI, but is it actually artificial intelligence? Click here to find out the truth behind ChatGPT.
Read MoreRevolutionizing Home Energy Management: The Partnership of Hub Controls and Four Square/TRE
Through a recently announced partnership with manufacturer Four Square/TRE, Hub Controls is set to redefine the landscape of home energy management in the U.S.
Read More4 Benefits of Time Tracking Software for Small Businesses
Time tracking is invaluable for every business's success. It ensures teams and time are well managed. While you can do manual time tracking, it's time-consuming and prone to errors. Tracking time manually also increases the risk of time theft and buddy punching. This is where time-tracking software …
Read MoreHow the Terraform Registry Helps DevOps Teams Increase Efficiency
A key component to HashiCorp's Terraform infrastructure-as-code (IaC) ecosystem, the Terraform Registry made it to the news in late 2023 when changes to its TOS prompted objections from open-source advocates. This was because the revisions initiated by HashiCorp were allegedly aimed at making it dif…
Read MoreNightmares, No More: New CanineAlert Device for Service Dogs Helps Reduce PTSD for Owners, Particularly Veterans
Canine Companions, a nonprofit organization that transforms the lives of veterans (and others) suffering PTSD with vigilant service dogs, has debuted its CanineAlert Device to more strategically target the lasting effects of trauma on an individual.
Read MoreIBM's AI Brings Data-Driven Insights and Spanish Narration to the Masters
The Masters Tournament and IBM announced new features for the 2024 Masters app and Masters.com, powered by watsonX.
Read MoreInnovating Organic Waste Management: John Gessin Explores Technological Advances in Green Waste Recovery
In recent years, there has been a growing awareness about the negative impact of traditional waste disposal methods on our environment. As a result, individuals and organizations have started exploring alternative ways to manage their waste, specifically organic waste. One such pioneer in this field…
Read MoreIceotope Reinforces Industry Leadership to Make the Most of Precision Liquid Cooling Solutions
Earlier today, Iceotope announced that it is officially welcoming Christian Belady as its new Senior Advisor. Moreover a new U.S. headquarters has been established in the Research Triangle Park (RTP) in Raleigh, North Carolina to open the door for greater collaboration opportunities with partners an…
Read MoreUnderstanding Cybersecurity Risks in Cryptocurrency Investments
There are many unique opportunities for investment in the cryptocurrency and blockchain industry. With several thousand different digital assets and a market cap of more than $2.5 trillion, crypto's position as a worthy asset class is undoubtedly strong. In addition, assets like Bitcoin (BTC) have r…
Read MoreCan Science Outsmart Deepfake Deceivers? Klick Labs Proposes an Emerging Solution
Researchers at Klick Labs were able to identify audio deepfakes from authentic audio recordings via new vocal biomarker technology (alongside AI models and machine learning).
Read MoreTop 5 Best Ways to Integrate Technology for Successful Project-Based Learning
Project-based learning, also popularly known as the PBL curriculum, emphasizes using and integrating technology with classroom teaching. This approach aims to achieve more effective learning and ensure the tech platform is at its best for proper implementation during the learning process!
Read MoreHow to Protect Your Website From LDAP Injection Attacks
Prevent LDAP injection attacks with regular testing, limiting access privileges, sanitizing user input, and applying the proper encoding functions.
Read MoreAzure Cost Optimization: 5 Things You Can Do to Save on Azure
Azure cost optimization is the process of managing and reducing the overall cost of using Azure. It involves understanding the resources you're using, how they are billed, and making adjustments to reduce costs while still meeting your IT needs.
Read MoreMassive Meta Apps and Services Outage Impacts Users Worldwide
Meta's suite of apps and services are experiencing major global outages on Super Tuesday 2024.
Read MoreThe Role of Technology in Shaping the Future of Affiliate Marketing
In the current rapidly growing digital world, affiliate marketing is still one of the most effective ways for businesses to increase their visibility on the internet and to create additional income. On the other hand, you should keep updated yourself with regards to the most current trends and new t…
Read MoreThe Steps You Can Take To Improve Customer Service For Your Business
When you're in a competitive market, providing exceptional customer service is crucial for the success and growth of your business. Good customer service fosters loyalty, improves brand reputation, and differentiates your company from the competition. This guide explores practical steps you can take…
Read More