While cyber-based maliciousness these days is never far from being front page/first look headlines, with the Black Hat USA 2012 event now going on in Las Vegas, the subject is justifiably intensely top of mind. Indeed, keeping track of the nature of threats and who might be behind them and where they are coming from is important. In that vein, the publication of Internet and mobile security provider, AVG Technologies’ Q2 2012 Community Powered Threat Report provides a fascinating snapshot into the world of cyber threats. For good and for bad, it is a page-turner.
As background, AVG has over 114 million actives users. The report is based on their Community Protection Network traffic and data, which is collected from participating AVG users over a three-month period and then analyzed by AVG. It provides an overview of web, mobile devices, spam risks and threats.
Food for thought
You should read the full report to obtain more granularities on specifics. Below are just a few findings that stand out as highlighted in the announcement of the publication. As you will see, focus this quarter is on how cybercriminals have combined social engineering with more complex malware authoring for PC and mobile to increase impact, and that many of these are emerging from China.
Android smartphone users remain a lucrative target: With 59 percent global market share this is too big of an opportunity to ignore. Much of the new malware has also been identified as originating from China and targeting users there and in neighboring markets, reflecting the fact that this is now the world’s top smartphone market with over one million mobile web users.
This quarter punctuated the China connection. For example, the first Android bootkit, ‘DKFbootkit’ appeared. It masquerades as a fake version of a legitimate application and damages the smartphone’s Linux kernel code by replacing it with malicious code. AVG notes that, “In rooting the device, this attack turns the smartphone into a zombie that is fully under the cybercriminal’s control, which makes it a serious threat to Android users. This attack is spread over the third-party applications market – and not the official Google Play - in China.”
The report also notes that there was a “return to grass roots.” Malware authors spammed China, Japan, South Korea, Taiwan and USA with Trojan-infected e-mail messages. Demonstrating the ingenuity at work, these were released on the back of a Microsoft ‘Patch Tuesday’ security bulletin to take advantage of the time delay between people getting the alert and actually implementing it. In this scheme, an e-mail attachment contains an embedded encrypted executable file which collects sensitive user information such as passwords. It can then download additional malware for key logger facility or to get a new Trojan configuration.
Yuval Ben-Itzhak, chief technology officer at AVG, said, “In our experience, an operating system attracts attention from cybercriminals once it secures five per cent market share; once it reaches ten per cent, it will be actively attacked. It’s no surprise therefore that our investigations uncovered a further upsurge in malware targeting Android smartphones, given its sustained popularity, with new attacks focused on rooting devices to give cybercriminals full control. What’s new this quarter is the upsurge in threats originating from China, emphasizing which markets appear to have a booming dark economy.”
A few other things were also worthy of note:
The end of antivirus? — Not so says AVG. In fact, while the security industry has adapted to the unexpected nature of threats but the growing sophistication of threats, like the Stuxnet virus, highlight the need for increased rather than decreased antivirus vigilance, and certainly the need to keep your definitions as current as possible.
Consumer scams — Deception reigns here with AVG citing the latest version of the LizaMoon mass injection SQL attack, which tricked users into downloading a Trojan or some rogue software by exploiting human interest and hiding inside non-existent celebrity sex videos or fake antivirus websites. I will be nice and say that “disappointed” users never saw the video as the malware installed a Trojan disguised as a Flash update. And, that is just one example of several that shows just how hard at work the bad guys are and how successful they can be in taking popular activities and sites and turning them into money makers for themselves. Indeed, it is sad to report that even the popular Angry Bird’s app was not immune as a Trojan-infected version was uploaded to unofficial Android application stores.
As noted, the report is filled with a wealth of information about the where, when, why, how and who (to the extent the country of origin is known) of various threats that are worth a read. As you think about risk management for your organization and the level of preparedness consider the following chart on the behavior categories of this past quarter:
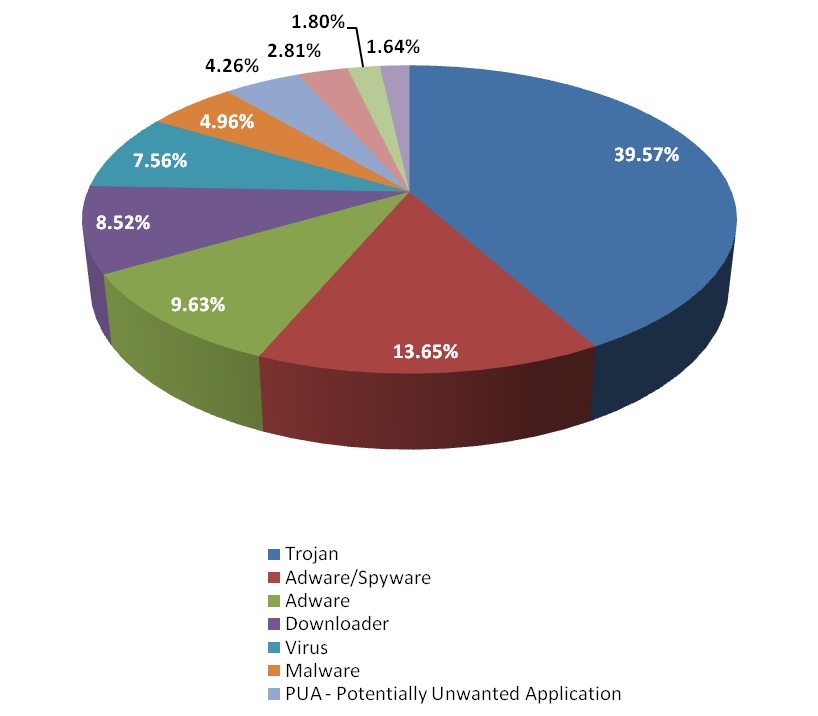
Source: AVG Technologies’ Q2 2012 Community Powered Threat Report
While no attack should be minimized in terms of the problems it can create, in light of the explosion of smartphones and tablets and their use in enterprises, i.e., the bring your own device (BYOD) phenomenon, the spike in threats going after the Android base — which runs the gamut from rooting tools to hacking tools and malware — presents a real challenge to IT departments.
Unfortunately, it is not like IT does not already have a full plate. On top of the growing sophistication of cyber attacks of all types, given just the authentication and administration (enforcement of policies and rules) for legitimate purposes of personal devices and the apps that run on them the vulnerabilities of such devices to being compromised is certainly another major headache. And, before all of the iPhone and iPad users get smug, be forewarned that Apple too now can be made rotten to the core by those with evil on their minds as recent events have shown.
Whether you are or are not a current AVG customer this report is one that you may wish to do more than just scan.
Edited by
Brooke Neuman