This week seems to be a good one for being worried about cyber attacks of all shapes and sizes. Earlier I posted an article on the miniFlame malware just discovered by Kaspersky Lab which is designed to steal data and control infected machines during targeted cyber-espionage operations. I was so agitated by that one that I started checking some of my favorite sites to see what else is brewing. Landing on MIT’s Technology Review site, I was not disappointed but was disturbed.
Two items caught my attention. Ironically one dealt with visualization (a map) and the other had to do with the lack of one.
What does a Botnet look like?
MIT Technology contributor Mike Orcutt, asked and answered the question in the above sub-headline. He presented a map created by security firm F-Secure which with the help of Google maps of the U.S. and Western Europe. It shows the spread of the notorious ZeroAccess malware. The author says security firm Sophos believes the malware has been installed roughly nine million times over the years with currently an army of almost one million infected computers.
FYI. This is a nasty one. It has evaded anti-virus programs as it has morphed over the years, and like other bay boys it connects infected computers to a peer-to-peer network so it can get commands to download even more malware. I speak from experience. This week, a certain someone in my family ran out of hard drive space. They were also getting weird messages when booting up. The installed anti-virus software found nothing. However, and industrial strength scan found seven virus which were busy loading up the computer. Thank goodness the hard drive was not damaged or needed to be replaced. But I digress.
Below is the map of the U.S., courtesy of F-Secure the one for Europe is equally bad. That is a lot of red.
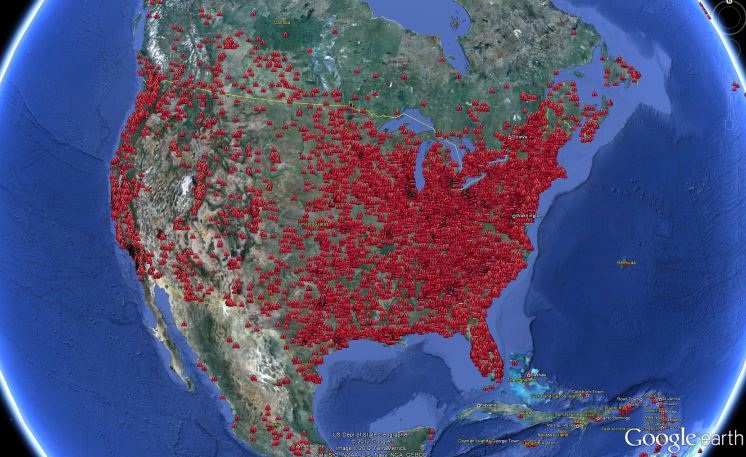
And, here is the link for the zip file containing the data. As they say in the texting world, OMG!
But wait, there is more bad cyber news
If that were not distressing enough, while perusing the rest of what is one of my favorite sites, what should appear but the following, Preparing for Cyber War, Without a Map. I was wondering who the author Tom Simonite had in mind until I read the sub-head, “The U.S. government has pledged to retaliate quickly if power grids or other critical elements of infrastructure are hacked—but the technology needed to do so is lacking.”
I will not go into all of the details discussed in the article. It referenced U.S. defense secretary Leon Panetta’s assertion that we will defend ourselves to the max in the face of cyber warfare, then raised a question as to whether we are prepared. This is where it got scary. Quoting extensively Joe Weiss, managing director of the International Society of Automation, it was noted that an electric utility could spot and reverse-engineer an attack on its office computers but would be hard-pressed to deal with an attack on the control systems that run the power grid.
The show stopper was Weiss saying: "You can't hide the lights going off, but you can sure be in a position to not know it was cyber that caused it." He even cited a 2008 example where three million people in Florida were without service by an incident that was eventually traced to one employee who disabled two protection systems.
Unfortunately, the picture painted was bleak. The U.S. is not alone in being unprepared for a sophisticated attack on our power grid because again quoting Weiss, “How do you secure a system that cannot be upgraded for security and will not be replaced in years?" he says. "You can't do to these systems what you would do in the IT world."
The points are well taken. They also are harrowing. Several years ago I attended a national security conference. The closing panel of experts was asked which of the following terrorist acts they most feared because of the amount of economic damage they could wreak:
- Cyber attack on the power grid
- Dirty nuclear bomb
- Contamination of a metropolitan area water supply
- A strategic chemical accident
- To a person they voted for choice #1.
I think I may have to stop visiting MIT Technology Review so often. It also may be time to take Ambien so I can get to sleep tonight. One can only hope that Weiss is not totally correct and that Panetta is not being overly optimistic and he and the utility industry are doing a lot more than meets the eyes of industry experts.
Edited by
Brooke Neuman