There has been a lot written about the Bring Your Own Device (BYOD) phenomena and how it is reshaping how we work and spend our leisure time. There’s even been some space invested in the fact that BYOD is a major driver behind the blurring of the distinction between the two in our 24/7/365 always on and all ways connected world.
That said, there remains some interesting questions as to BYOD, regarding how much and how often our smartphones and tablets are used for work, whether end users believe their companies are ready for BYOD, and how many companies are helping employees purchase such devices.
The good news is a network of Cisco partners set out to find answers to all of these questions, and a few more, and the results of their interviews with 1,000 consumers (spearheaded by Cisco partner firm Pine Cove of Billings, MT) about mobility and their employers BYOD policies, are now available. Reader alert! There are some surprises here.
BYOD is shaking things up in enterprises
Let’s get right to the highlights:
- 62 percent of U.S. employees who use their own smartphone for work do so everyday
- 92 percent of U.S. employees who use their smartphones for work did so this week
- Only 6 percent of workers say their employers paid for the smartphone outright with 3 percent saying they get a stipend and 11 percent saying they get a small reimbursement
- 84 percent of employees report their employers would not replace their personal devices if lost or broken even though an almost equal percentage uses their personal device for work purposes
- 39 percent of workers who use personal smartphones for work don’t password protect
- 52 percent access unsecured WiFi networks
- 69 percent of BYODers are expected to access work emails after hours
- Only 46 percent believe their employers are prepared for any issues that could arise from BYOD
Here are just two graphics from the report that illustrate the challenges BYOD presents, and give a flavor of BYOD by industry sector.
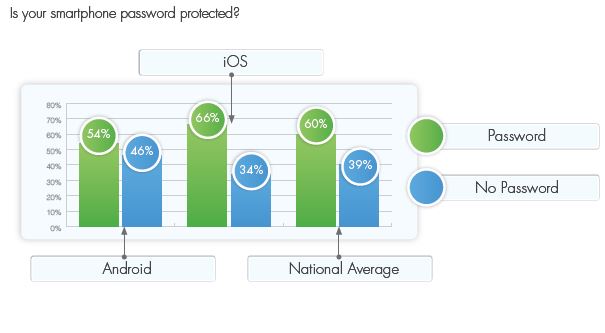
Source: © Cisco mConceirge 2013
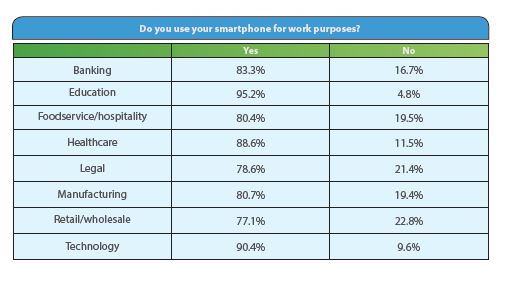
Source: © Cisco mConceirge 2013
In a word, YIKES! We are all on our own basically for the purchase of our personal device, use them increasingly for work and have extended when and how we work by using BYOD “after hours.” In addition, we seem to be relatively lax in terms of our securing them when they’re in an work mode (i.e., are creating a nightmare for IT by bypassing them through remote and WiFi use and the lack of password protection), and believe our employers are not capable of protecting themselves from our use of such devices even, as we are tacitly encouraged to use them for a variety of reasons.
Plus, the context for all of this is that the number of adults who report having a smartphone jumped 12 percent in 2012 according to the Pew Center. And, as the report correctly points out, “As that number grows and more Americans return to the workforce in the recovery from the Recession, BYOD will cause security breakdowns and cost companies money…Knowing some of your employee’ smartphone habits can help you prepare to mitigate the impact of those events.”
In short, while we are still early into the learning curve of the impact that BYOD can have on users as well as enterprises – and the costs and benefits of BYOD proliferation – the impacts in just a very short period of time are profound.
It should be noted that all of this will be the subject of a TMC special event, “SecureIT: Protecting Your Enterprise in a BYOD World,” that will be taking place July 23, 2013 at the NYU Kimmel Center, New York, NY. Mark your calendars to save the date. Program details will be available in the next few days on this topic that has everyone looking for information and answers.
Edited by
Braden Becker