Recently, the headlines have been about Distributed Denial of Service (DDoS) attacks, governments blocking Internet access and organized criminals as prime suspects in perpetrating cyber mischief of all types. Plus, every day sees more and more brand names having critical information stolen or their websites compromised.
However, the facts are that as a result of the Bring Your Own Device (BYOD) era, virtualization and the proliferation of Cloud-based services, as some have cleverly opined, we are now also in a Bring Your Own Danger (the dark version of BYOD) era. We use our devices, which may or may not be authenticated for corporate use, to access unauthorized apps and content and send things over unprotected networks. In short, we want what we want when we want it, and circumvent IT in getting it or engage in unprotected interactions. In many ways, we are our own worst enemies and we have placed enterprise IT in the unenviable position of being accountable for better security in an increasingly complex world, but without helping them as users or giving them the tools they need to mitigate risks as executives with budget authority.
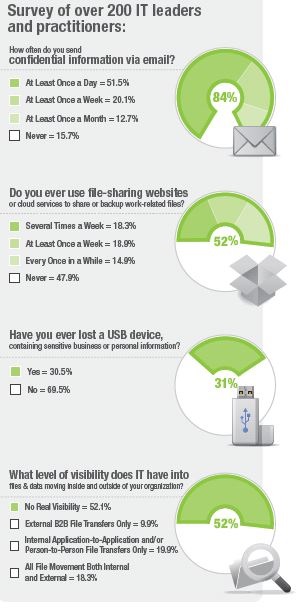 In discussing all of this with Jeffrey Whitney, vice president, global marketing, he drew my attention to a recent Ipswitch survey that put all of this in stark relief.
In discussing all of this with Jeffrey Whitney, vice president, global marketing, he drew my attention to a recent Ipswitch survey that put all of this in stark relief.
As Whitney noted, “In short, we have users behaving badly or poorly either intentionally or more often unintentionally, and IT with limited visibility into what is going on. This is a recipe for disaster. ” He added that while things like DDoS and malware get the media’s attention, “CSOs (chief security officers) need look no further than file transfers, which make up a significant amount of critical information that is on the move inter and intra-enterprise, to see how serious their data leakage exposure is and why they need to take actions now to mitigate the risks.”
More details of the survey are contained in an Ipswitch e-book, Are Employees Putting Your Company’s Data at Risk? What resonate are the recommendations summarized below.
“Companies are struggling to strike the right balance between productivity and security, particularly as more employees work remotely. Employees want simplicity and convenience, while IT managers require visibility, security and control. IT leaders and practitioners need to understand the benefits, risks, and consequences associated with the proliferation of personal file transfer and file sharing tools…IT managers need to make it easier for people in the organization to move information securely. What most companies don’t yet realize is that they no longer have to choose between the two extremes…Rather than fighting a losing battle, companies should revisit their security policies and gauge whether they are appropriate for what employees are trying to accomplish.”
At the end of the day, nothing can be made totally secure for two reasons:
Those with malicious intent will find a way to cause trouble if the incentives are high and the risks and also the costs of failure are low. It is why the bad guys are always probing for weaknesses to exploit. BYOD, particularly when it comes to file transfers, be they e-mail or using third-party services like Dropbox, make for easy targets.
Security starts and ends with people, and people are fallible—we forget things, we make well-intentioned but poor choices, we opt for convenience and expediency without consideration of risks to our employers, etc.
It is why that term “balance” is so critical in any discussion of enterprise security. The goal is to make the needs of users and IT mostly mutually inclusive while making it too hard, expensive or both for those with bad intentions to target and succeed in disrupting that which we highly value.
This is why BYOD is seen as having forced the issue on getting IT and upper management to evaluate digital risk mitigation from a strategic as well as tactical perspective and why a holistic approach, which includes for lack of a better term “triaging” various assets based on the level of risk they carry, along with providing users education and easily embraceable polices and tools they can use to exponentially decrease risks are key.
The issue of file transfers is just one of the featured talks that will be given at TMC’s, “SecureIT 2013: Protecting Your Enterprise in a BYOD World,” event that will be held July 23, at the Kimmel Center of NYU in New York City. Keep your eyes open for more information about the program and speakers in the coming days. We look to see you there.
Edited by
Brooke Neuman