Several somebody’s had a very good first quarter of 2013. Unfortunately, according to the recently released threat report by McAfee Labs, the individuals having a good quarter were the bad guys. That certainly is not good news for any of us.
The introduction to the report says it all. McAfee Labs researchers saw things that were all too familiar. These included:
- Steady growth in mobile malware
- A rapid increase in general malware, including Facebook threat Koobface, AutoRun malware, and stealth malware that attacks the master boot record (MBR)
- Worldwide spam doubled during the quarter—making a comeback after more than a year of decline.
And, if that were not enough that noted that while the financial sector has been rampant with narrowly targeted attacks, “…one came with a twist. Our analysis of the Citadel Trojan shows that cybercriminals have found a way to turn this traditional bank-account threat into the broader theft of personal information from narrowly targeted victims in certain countries.”
McAfee paints a sobering picture on cyber threats
In my coverage of these reports from various companies in the security business, the word “sobering” is one that always seem appropriate. As the researchers note, “All malware that we track—affecting clients, servers, networks, mobiles—now stands at more than 128 million samples. That figure has climbed steadily for ages and quite rapidly during the last two quarters. Koobface, along with AutoRun, ransomware (when bad actors literally use the threat of cyber destruction to extort tribute to not go through with an attack or to release you if your enterprise is already ensnarled) and MBR threats were the leaders this period.
Plus, they acknowledge that when it comes to ransomware, there are no guarantees that if you pay you are inoculated from further mischief by the same perpetrators, and anonymous payment systems make it almost impossible to track the extortionists’ movements. The nastiness of MBR threats is well known, and the real threat is that they can remain on a system for a long time and do real damage, including downloading other types of malware.
While it is not the intention to cause nightmares, just two graphics from the report are worth a look. First is the size, scope and speed at which bad things are evolving.
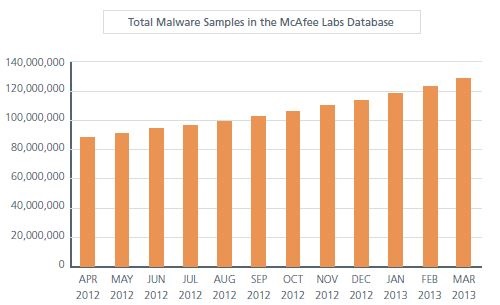
Source: McAfee Threats Report: First Quarter 2013
This is not a case where “the trend is your friend.” Although, one can argue that the fact that McAfee has all of these samples is an indicator that the good guys are on the case and that keeping current on protection against many if not all of the problem children that invade our businesses and homes should give us a little piece of mind. The problem is that when you get into the details of the report, particularly in regard to the explosion of mobile malware aimed mostly at the Android ecosystem (partly a reflection of who has McAfee for a defense), that relative peace of mind evaporates.
From the perspective of the source and targets of network threats, despite all of the headlines about China, Russian criminals, etc., the report found that on the network side of things, IP addresses in the United States are again both the source and the target of most malicious network activity. It also found, as the graphic shows, that browser-based attacks, such as hidden iframes and malicious Java code, are the most common type.
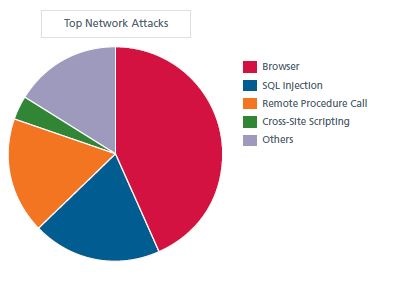
Source: McAfee Threats Report: First Quarter 2013
The report contains details about each of the pieces of the pie above but they all show the same thing, e.g., no matter the type of attack, the U.S. is where the action is. This is not surprising based on the old quotation by infamous U.S. bank robber Willy Sutton who, when asked why he robbed banks, said, “That is where the money is.”
What the researchers concluded with was some food for thought. The bad news they feel, rightfully, is that cybercriminals continue to develop and market crimeware tools. The entrepreneurial aspects of this are particularly alarming because it has made the barriers to entry in the bad actor business a lot lower and they appear to have lots of new takers. The good news they cite is that European Union’s new European Cybercrime Center has been instrumental in aiding law enforcement to arrest and prosecute online criminals. Not cited in the report is that the level of cooperation between international law enforcement agents and those in the cyber protection business has improved in terms of the sharing of information along with better visibility into what is actually going on in real-time.
The thirty-five page report has not only interesting data on threats, but also some interesting observations about the increasing use of cyberthreats by “Hacktivists” like the infamous group Anonymous, which has raised the possibility of using distributed denial-of-service attacks (DDoS) as lawful means to support their ends, and the impact of so-called cyberarmies who, especially in the Middle East, are using/abusing the Internet in countries that limit personal liberties and claim when they silence speech that they are acting on behalf of their governments to help maintain civil order.
If anyone needed confirmation on why cyber threats are now viewed around the world as being likely more damaging than conventional warfare in terms of economic destruction and the ability to cripple individuals as well as corporations, that first graphic above says all that needs to be said. Malicious behavior online continues to surge, and it is a threat that is impossible to over-estimate.
Edited by
Rachel Ramsey