For anyone looking at recent headlines, it is more than crystal clear that state-sponsored cyber attacks are on the rise. Whether it be China, North Korea or a growing list of others, the use of online tools to compromise companies and government agencies is not just a fact of modern life but something many security experts have stated is the number one threat to national and enterprise security. And, with the Syrian Electronic Army already fingered for attacks on various U.S. media outlets in just the past few days, it is also clear that cyber terrorism is increasingly the choice of those who wish to have profound impact on countries and companies they view as the enemy.
Interestingly, the threat of Syrian reprisal to a looming missile attack on the part of the U.S. and possible allies coming via cyber space has strangely not been a subject of public conversation. We can only hope that is a chapter that will go unwritten.
What the concern about cyber terrorism has raised is the interesting question as to whether enterprises, particularly in the U.S., feel they are prepared to defend themselves. To get some perspective on this question, Lieberman Software, who counts amongst its identity management and security management customers many of the Fortune 50 companies, surveyed 200 senior IT security professionals at the Black Hat USA 2013 event recently in Las Vegas. To put it mildly, the view from the pros is troublesome.
It is going to get worse, and the IT professionals feel we are losing the war
Let’s start with the headlines from the survey:
- 58 percent of respondents believe we are losing the battle against state-sponsored attacks
- 74 percent are not even confident that their own corporate network has not already been breached by a foreign state-sponsored hacker
- 96 percent believe that the hacking landscape is going to get worse over time
Other key findings that should give everyone pause are shown in the two graphics below which should be more than enough to make you want to download the full report.
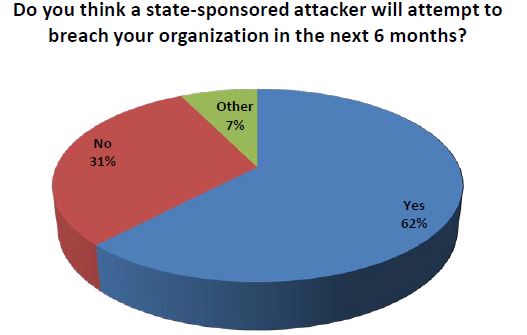
Source: Lieberman Software 2013 Survey of Information Security Professionals
And, if that is not sufficient to scare you the next one will really give you pause.
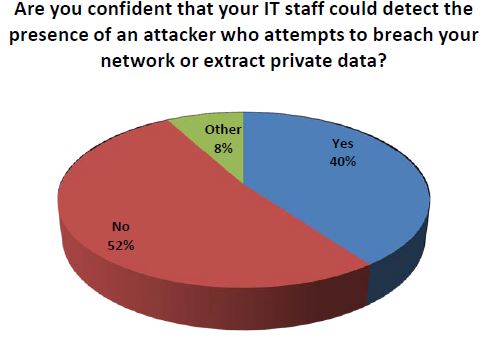
Source: Lieberman Software 2013 Survey of Information Security Professionals
Commenting on these findings, Amar Singh, ISACA Security Advisory Group London Chair, said “I would have imagined the figure to be higher than 58 percent because most organizations will lose the battle if they end up on the target list of a state-sponsored attacker. The icing on the cake, from the malicious hacker’s perspective will be when the world fully embraces IPV6, the next generation internet protocol that will allow every single human being on this planet to own at least 2000 fixed and permanent cyberspace addressees. Think about the attack surface when your TV, watch, wristband and car’s engine have a unique cyber space address and will be always connected to cyberspace!”
This is truly nasty business and a lot of resources are being thrown at preparing nations to be offensive as well as defensive in developing cyber attack measures and counter-measures. For example, as Lieberman notes, North Korea announced it has built an army of 3,000 cyber trolls to attack South Korean websites.
Philip Lieberman, President and CEO of Lieberman Software, said “The threat of state-sponsored attacks is extremely serious for government and commercial entities. The probing of IT infrastructures in both environments is occurring 24/7, with attacks being launched on a regular basis. These types of attacks are very difficult to stop, almost impossible to attribute to a specific country, and a pain in the neck to anyone who gets caught in the middle of their battles. We cannot stop these attacks; we can only build taller and thicker walls to keep the hordes out.”
“The majority of organizations are prepared for amateur hackers and low-level criminals, but are completely ill-equipped to deal with today’s advanced nation-state foes. The most dangerous threats are highly personalized attacks designed for one-time use against specific individuals. Many state-sponsored attackers can now create perfect email attacks that insert remote control software onto corporate networks. Most corporations and government agencies would benefit from better security training, documented security processes, and enterprise-level products that can manage and secure powerful privileged accounts that grant access to critical IT assets,” Lieberman continued.
It goes without saying that, given the beliefs of the respondents, Lieberman’s conclusion that “we ain’t seen nothing yet,” is something that not just government officials but C-levels need to take seriously. When your own IT department believes that you are likely to be attacked and are not really prepared to defend, one would hope you do not end up in the position of hearing, “I told you so!”
The one piece of relatively good news is that respondents did indicate their organizations were becoming more proactive in shoring up their defenses. They were asked which additional security precautions their organizations’ had taken: user training, security appliances, end point testing or pen testing. 69.7 percent replied that they use all of these security measures, while only 1.1 percent stated that they do not use any of them. In fact, another reason to read the survey results is to see the individual breakdowns of these areas.
The message here is not that it would be prudent to be safe rather than sorry. That goes without saying. The bigger message is that it is time for enterprise stakeholders from across the company to engage IT in a frank discussion as to what can and should be done, in what order to reduce risks in the short-term and how to develop a strategy for making longer term security investments based on the prognosis that, in fact, things are going to get a lot worse. The results may be sobering, but the lessons to be drawn cannot and should not be ignored.
Edited by
Blaise McNamee