It is Friday, and TGIF (Thank God it’s Friday!) certainly seems apropos. I knew it was too good to be true that I would get through a week without writing about the level of responsiveness of a major tech firm in crisis mode over a malfunction of some sort—data breach, DDoS attack, invasion of malware by alien bots, etc. The bad news is that Adobe was the one this time that got hit, and as this is written is still in the midst of a continuing saga that may have started back in August concerning the compromising of possibly 2.9 million customers’ names, encrypted credit and debit card numbers, and source code. Ooops!
The somewhat good news is that Adobe seems to have learned a few things from the lack of appropriate crisis management behavior by other big tech firms recently, and the Adobe acrobatics should stand them in good stead on the trusted brand level going forward. They may not have been perfect in dealing with customers, but they have been quite good.
The truth is that I have lost count of how many times I have had to report on cyber issues of all types involving everything from service disruptions to major security breaches in just the past few months. Do headlines about Google, Amazon, Microsoft, and Twitter just to name a few, sound familiar? And, I am not referring to any connection these “instances” may have to the ongoing NSA scandal.
What the industry cyber issues have had in common to this point is the victimized company’s inability to keep customers in the loop. This time it has been pleasingly a bit different.
What we know now
It is not my purpose to go over ground that has been covered by a myriad of others in the blogosphere. I can say that the best timeline of all of this was posted by Matt Peckham on Time Tech.
To summarize the summary, last week blogger Brian Krebs and security firm Hold Security found Adobe source code in the hands of folks who should not have had it. They notified Adobe, which ‘fessed up this week that they knew last week, and identified the data that was compromised as in fact source code for most of Adobe’s products and that customer proprietary information including payment info had been compromised.
Yesterday, Brad Arkin, Chief Security Officer, posted an “Important Customer Security Announcement” on Adobe’s featured blog site.
As these types of messages go, this is a good on two scores. They actually posted something, heretofore an exception not the rule. Second, in a case of better late than never, they tell you what steps they are taking to deal with the issues, including (OMG!) notifying customers they believe may have had their debit and credit information swiped. In fact, look at the second bullet. They are offering victims the option of enrolling in a one-year complimentary credit monitoring membership where available. It almost made me wish I had paid them for something.
It gets even better. Go to Adobe.com and look at the home page
Do not stop there. Click the “click here”. Who would have thunk it? Useful information is at hand.
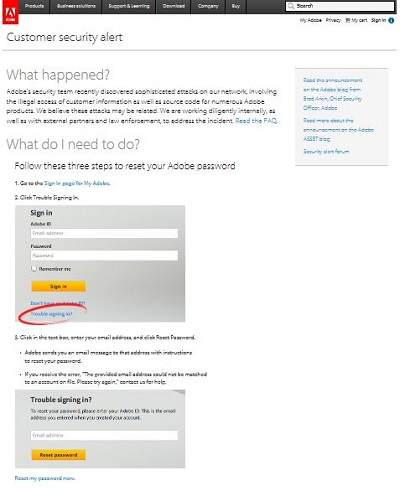
This is just part of the page. There are even (another OMG!) FAQs.
This is serious business
I would be remiss if I did not share a few insights that flooded my inbox from my friends in the security business. Bala Venkat, CMO, Cenzic noted that, “Unfortunately, Adobe's breach involves the theft of its source code, which isn't something we see that often. Beyond the usual loss of customer user names and passwords, Adobe has lost their 'crown jewels' and because every enterprise worldwide uses Adobe in one way or another, the impact is enormous."
"Regardless of how sophisticated these attacks may seem, the end game of this breach once again illustrates how vulnerable the application layer remains today. The most sensitive data and customer information resides in the databases and the hacker is looking for that one open vulnerability in the application to get to the precious data. More applications moving to the Web, cloud and mobile today further heightens the threat vector.
Organizations must take a proactive approach toward enforcing tight security processes right from the code development phase and through the entire SDLC (Software Development Life Cycle). It is paramount for developers to do thorough security checks on the applications before they are pushed into production. “
Like I said, Venkat’s thoughts are representative of a flood of similar ones from security pros from numerous companies TechZone360 covers concerning enterprises taking precautions to mitigate risks at every potential vector of vulnerability. Rajesh Ramanand, CEO of Signifyd, an eCommerce fraud prevention solution provider, added that the stolen credit card numbers alone could be worth up to $30 million on the black market, with the potential risk to customers being much higher.
In short, companies need to do a better job in being proactive about risk mitigation, and as vectors of vulnerability increase so are the rewards; cyber attacking has become big and very profitable business.
The best news to come out of all this is that the industry is finally developing and using better practices for keeping us informed when bad things happen. Adobe has not been perfect. In fact, if you check out their corporate and customer care Twitter feeds, you will see there is certainly room for improvement. In addition, considering I seem to get an update alert from them almost every day for the Adobe capabilities I do rely on, an e-mail would have been nice even if I am not a paying customer. The reason is that based on what we know, it is possible one of those updates could have contained malware.
On that last one I guess we will all just have to wait and see, but given how Adobe has conducted itself thus far hope springs eternal. The message to the tech industry is very clear, LEARN FROM THIS!
Thank you, Adobe.
Edited by
Rory J. Thompson