This posting needs to come with a reader warning so here it is. Please take an antacid, make that two, before reading any further.
It should be good news for all of us that the good folks at Cisco are out with The Cisco 2014 Annual Security Report. However, the only good news appears to be for bad actors. According to the detailed report, and in what has been an oft-repeated refrain from all of the security vendors on numerous fronts, the bad guys enjoyed a banner year.
As Cisco is detailing, in 2013 there was unprecedented growth of advanced attacks and malicious traffic that unfortunately reached historic levels. And, if that was not bad enough, the report notes that in the face of increased attack surface exposures, exponential improvements in attack sophistication, more widespread use of state of the black art monetization techniques by attackers, and involvement of rogue states, there is a worldwide shortage of nearly a million skilled security professionals.
In short, while defense tools are improving, the lack of skilled security professionals across all of the security practice areas is impacting organizations’ abilities to monitor and secure networks.
Now is the time to take a deep breath since there is an OMG moment. There is every reason to believe 2014 will be as bad and more likely worse than 2013. Those with malicious intent and capabilities are constantly exploring more diabolical ways to undermine trust and commerce. This is true whether their intentions are political, commercial, or both.
Indeed, it is depressing to note that hacking has become one of the great growth areas of the information age. It seems to always be on the cutting edge of innovation covering all the bases, i.e., who, what, where, when, why, how (fast, long, and for how much). Given, both how lucrative this activity is, and the low risks or consequences of getting caught, putting aside a lack of young workers being educated as security experts for a moment, the allocation of brain power on security issues is certainly something to contemplate when evaluating who has the resources to win cyber warfare.
News and views you can use
As noted, there is a lot to try and digest as usual in the report. In fact, the addition recent acquisition Sourcefire by Cisco makes this edition the report that much more insightful. What is striking is the complex and dynamic picture it paints of just how rapidly security challenges facing businesses, IT departments and individuals are evolving. As Cisco details, attacker methods now include socially engineered theft of passwords and credentials, hide-in-plain-sight infiltrations, and exploitation of the trust required for economic transactions, government services and social interactions.
“Really insidious stuff”
In fact, Cisco Threat Technical Leader Levi Gundert, told me that one of the most alarming trends the Cisco security team is watching, “A shift in the criminal attacker space away from end points to going after core Internet infrastructure.” He continued, “The shift helps complicate finding out the threat source, gives attackers broader reach, and looks legit to the end users. It is done through things like compromising SSH, and modifying HTTP software. This is really insidious stuff. The threat actors have rethought how they launch attacks. Hosting companies because of the layers of resellers can’t identify owners, and the attacks scale nicely. This is really insidious stuff.”
Before getting to some of the more insidious highlights, or low lights, depending on your view of things, the graphic below is a good visualization of what Gundert said about the shift in infection strategy and why it works so well.
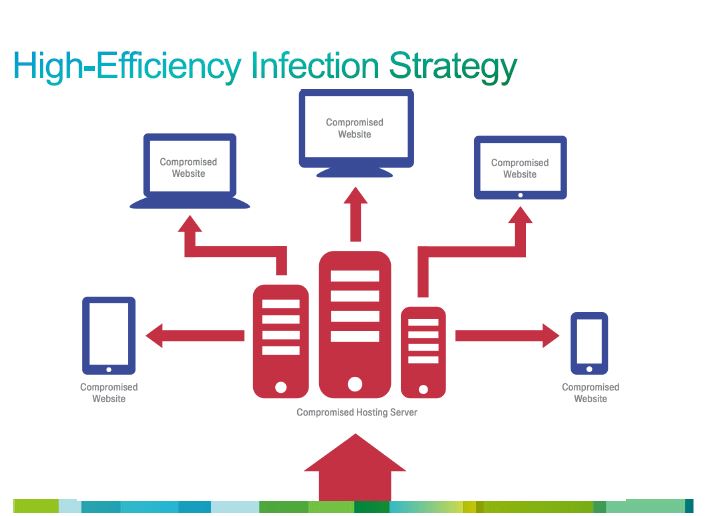
Source: Cisco Annual Security Report 2014
As to the things to look for when you read the report, there are a long list of things which all are relevant and summarized by the authors as follows:
- Increased sophistication and proliferation of the threat landscape. Simple attacks that caused containable damage have given way to organized cybercrime operations that are sophisticated, well-funded, and capable of significant economic and reputational damage to public and private sector victims.
- Increased complexity of threats and solutions due to rapid growth in intelligent mobile device adoption and cloud computing provide a greater attack surface than ever before. New classes of devices and new infrastructure architectures offer attackers opportunities to exploit unanticipated weaknesses and inadequately defended assets.
- Cybercriminals have learned that harnessing the power of Internet infrastructure yields far more benefits than simply gaining access to individual computers or devices. These infrastructure-scale attacks seek to gain access to strategically positioned web hosting servers, name servers and data centers—with the goal of proliferating attacks across legions of individual assets served by these resources. By targeting Internet infrastructure, attackers undermine trust in everything connected to or enabled by it.
- Overall vulnerabilities and threats reached the highest level since initial tracking began in May 2000. As of Oct. 2013, cumulative annual alert totals increased 14 percent year-over-year from 2012.
- The report indicates a shortage of more than a million security professionals across the globe in 2014. The sophistication of the technology and tactics used by online criminals—and their nonstop attempts to breach networks and steal data—have outpaced the ability of IT and security professionals to address these threats. Most organizations do not have the people or the systems to continuously monitor extended networks and detect infiltrations, and then apply protections, in a timely and effective manner.
- One-hundred percent of a sample of 30 of the world’s largest Fortune 500 company networks generated visitor traffic to Web sites that host malware. Ninety-six percent of networks reviewed communicated traffic to hijacked servers. Similarly 92 percent transmitted traffic to Web pages without content, which typically host malicious activity.
- Distributed denial of service (DDoS) attacks—which disrupt traffic to and from targeted websites and can paralyze ISPs—have increased in both volume and severity. Some DDoS attacks seek to conceal other nefarious activity, such as wire fraud before, during or after a noisy and distracting DDoS campaign.
- Multipurpose Trojans counted as the most frequently encountered web-delivered malware, at 27 percent of total encounters in 2013. Malicious scripts, such as exploits and iframes, formed the second most frequently encountered category at 23 percent. Data theft Trojans such as password stealers and backdoors made up 22 percent of total web malware encounters. The steady decline in unique malware hosts and IP addresses—down 30 percent between Jan. 2013 and Sept. 2013—suggests that malware is being concentrated in fewer hosts and fewer IP addresses.
- Java continues to be the most frequently exploited programming language targeted by online criminals. Data from Sourcefire, now a part of Cisco, also shows that Java exploits make up the vast majority (91 percent) of indicators of compromise (IOCs).
- Ninety-nine percent of all mobile malware targeted Android devices. At 43.8 percent, Andr/Qdplugin-A was the most frequently encountered mobile malware, typically via repackaged copies of legitimate apps distributed via non-official marketplaces.
- Specific business sectors, such as the pharmaceutical and chemical industry and the electronics manufacturing industry, historically have had high malware encounter rates. In 2012 and 2013, there was remarkable growth in malware encounters for the agriculture and mining industry—formerly a relatively low-risk sector. Malware encounters also continued to rise in the energy, oil and gas sectors.
As noted, this is a lot to digest, but there is one other chart from the report that is worth a quick look.
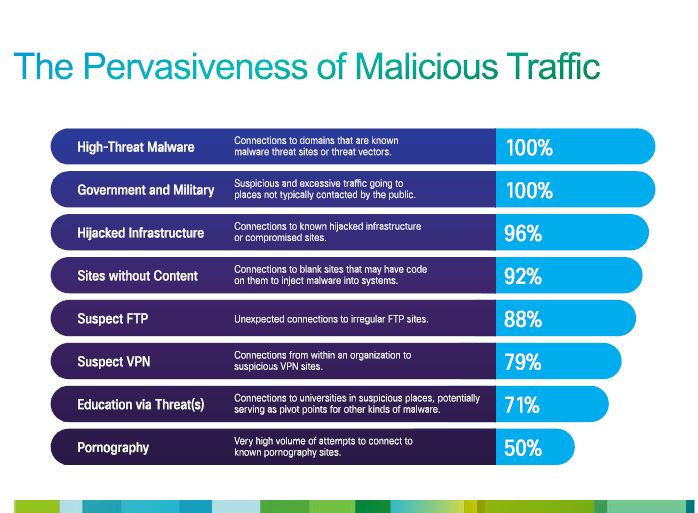
Source: Cisco Annual Security Report 2014
The takeaway is that organization is immune from being attacked and the probability is substantial you and your organization will be.
John N. Stewart, senior vice president, chief security officer, Threat Response Intelligence and Development, Cisco, had this to say about the findings: “Although the Cisco Annual Security Report paints a grim picture of the current state of cyber security, there is hope for restoring trust in people, institutions and technologies – and that starts with empowering defenders with real-world knowledge about expanding attack surfaces. To truly protect against all of these possible attacks, defenders must understand the attackers, their motivations and their methods – before, during and after an attack.”
I will not spoil your reading of what I keep handy on my hard drive for easy reference, but do not just look at the facts. Read through the recommendations which include:
- Organizations need to come to an agreement as to what is most important from a cybersecurity perspective.
- Organizations need to examine their security model holistically and gain visibility across the entire attack continuum.
- Technology vendors must help assure customers that security is a priority in their manufacturing processes—and be prepared to back up those assurances.
- One million security professional shortage across the globe in 2014. Many organizations need to find the people who can build and help utilize the systems necessary for timely and effective monitoring to address attacks before, during, and after.
In addition, if you wish to learn more and question in real-time John Stewart and Levi Gundert, Cisco is hosting a live broadcast with the two on Friday, Jan. 17 at 10:30 AM PT.
I resonate with Mr. Stewart about the need for better education and the need to take a posture that is more proactive and not just reactive in dealing with risk assessment and mitigation challenges.
This means as the recommendation highlight, getting not just security experts but C-levels across organizations to examine their security capabilities and model a reasoned holistic strategy for gaining visibility and knowing what to do about the entire attack continuum. It also means there is a lot of real education to be done so that the good guys can close the talent gap.
It may seem like a keen grasp of the obvious point on my part, but from both a technology and people perspective, you should not enter a gun fight bearing only a knife. The odds of success tilt very much in favor of the opposition. There are many reports from various sources that are sounding wake-up calls to all of us, and particularly upper management, about security threats. The recent data breaches at Target and Neiman-Marcus only punctuate the sense of urgency for actions since clearly staying the course or doing nothing is not an alternative.
I you are an IT security professional, you might wish to socialize this report. Fear truly can be a great motivator.
Edited by
Ryan Sartor