The annual conclave of many of the highest profile global political and economic leaders is now underway in Davos, Switzerland. There are certainly a significant number of weighty issues for those attending to address, and this year at the top of the list of things host the World Economic Forum (WEF) wants the group to focus on is cyber security. In fact, the subject has been a major concern for WEF who has a very salient report on it that was done in conjunction with Deloitte back in 2012, Risk and Responsibility in a Hyper Connected World: Pathways to Global Cyber Resilience. Hopefully, the leaders and their advisers have had a chance to scan if not read in its entirety.
The reason this is critical is that back in mid-2012 there was a prediction that a failure to boost cyber security could cost the world economy a staggering $3 trillion over time. Since the report’s publication the proof points of the gravity of the problem have only multiplied. In just the past several months, as if we needed further confirmation, the ripple effects of the Snowden leaks and the seemingly daily bad news on the increased frequency and sophistication of bad actors, be they criminal or state-sponsored, has made the seemingly implausible prediction seem almost conservative.
Doctor heal thy self
It will be interesting at the end of Davos to see if there are communiqués and action items related to cyber security. As the event starts, however, there is more pressing news. I was notified by my friends at Swiss security solutions provider and online watchdogs, High-Tech Bridge that their non-profit research lab—in exercising their innate curiosity for finding ways to keep the Internet safe as they were preparing their annual report on cyber attacks—had stumbled on problems with the online presence for the WEF event. In short, the WEF by not taking all of the necessary precautions was providing a great opportunity for those with malicious intent to launch highly visible mayhem.
The details for those wishing to really dive into the weeds are contained in High-Tech Bridge’s new blog that explains the three vulnerabilities it found. One was an XSS vulnerability on a WEF sub-domain, and
there were two XSS vulnerabilities on their main website.
Thus far the exploits have not been attempted, but obviously there is still time. The good news is the blog does provide proof of concepts. It also informed the WEF of the issues. However, they say, “High-Tech Bridge informed WEF of its discoveries last week and has heard nothing back. In an attempt to find another relevant contact at WEF, High-Tech Bridge found a more sinister vulnerability which allows access to email addresses which would be advantageous to spammers.”
It was five days yesterday that High-Tech Bridge had not heard back from the WEF, and hopefully as this goes to publication that is no longer the case.
As noted, the blog is quite thorough in its descriptions. I will not spoil readers’ fun/horror in going through the details but as a teaser here are three screen shots.
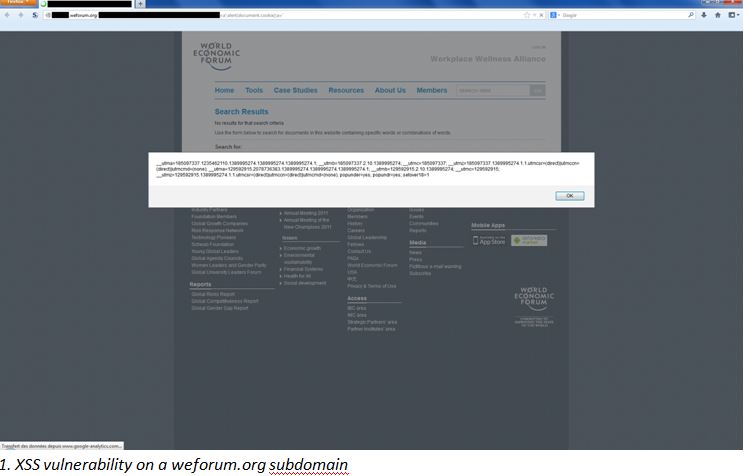
The above was on the researcher’s first pass at possible problems. As they explain: “A quick and absolutely harmless test of their main website [www.weforum.org] revealed two more XSS vulnerabilities on it”:
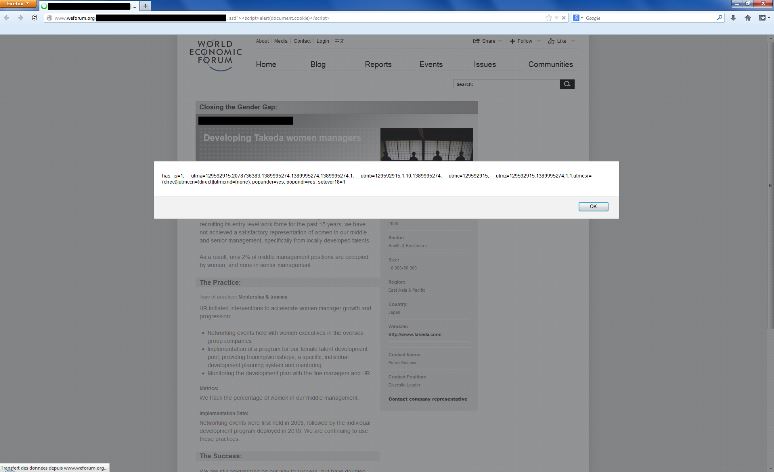
2. XSS vulnerability on www.weforum.org
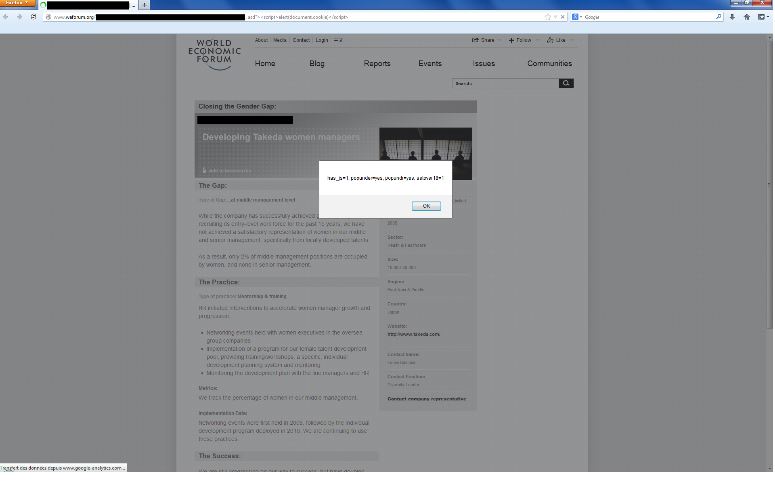
3. XSS vulnerability on www.weforum.org
Ilia Kolochenko, High-Tech Bridge’s CEO, commenting on the findings stated: "It’s regrettable that such respectable, large and important organizations like the WEF don’t pay enough attention to web security. This may not only put their own infrastructure at risk, but their stakeholders as well…Moreover, the vulnerabilities we reported are quite possibly just the tip of iceberg, as without their [WEF] permission we didn’t want to perform any further more “intrusive” security checks that can reveal much more serious vulnerabilities. I sincerely hope that these vulnerabilities were not exploited by hackers for whom WEF and its participants are very attractive targets."
It seems there is an outbreak of incidents where organizations are caught in a situation of, “Do as I say, and not as I do.” As I note recently Google changed Google Alerts without sending users an alert. Now we have what is arguably the most prestigious gathering of world power brokers intent how assuring trust in the Internet so the digital economy can continue to grow, not taking seemingly even simple steps to protect the event website.
What High-Tech Bridge has exposed is the continued chorus coming out of the security industry. At the highest levels of government and commerce there is a lot of talk about the gravity of cyber security and the need to be more vigilant, proactive and master to respond. Unfortunately, as recent events highlight, we still seem to have a significant gap between words and actions. Indeed, the WEF should be embarrassed on two fronts. The first is the obvious one that they clearly did not institute best practices to protect their online presence. This would almost be funny if it were not true. The second is more sobering, i.e., why take so long to respond to High-Tech Bridge? Maybe one of the tech luminaries at Davos could help find the answer to that mystery.
Edited by
Cassandra Tucker