For those of you who like myself are avid followers of all things related to online security you know it is report season. And, while all of the reports from various security vendors provide valuable information on various aspects of cyber security and risk mitigation recommendations, to my mind the gold standard for really getting a fix on what is going in regards to data breaches, comes from Verizon.
The good news is Verizon’s “2014 Data Breach Investigations Report,” is now available for download. The bad news, as Wade Baker, principal author of the Data Breach Investigations Report (DBIR) series, says is that: “After analyzing 10 years of data, we realize most organizations cannot keep up with cybercrime – and the bad guys are winning.”
Before you get too apoplectic, Baker does add, “But by applying big data analytics to security risk management, we can begin to bend the curve and combat cybercrime more effectively and strategically….Organizations need to realize no one is immune from a data breach. Compounding this issue is the fact that it is taking longer to identify compromises within an organization – often weeks or months, while penetrating an organization can take minutes or hours.”
A comprehensive look at very bad behavior
In its seventh year of publication, the reasons why the DBIR is the go-to resource when it comes to data breaches is the comprehensive nature of the research effort which benefits from contributions from over 50 organizations from around the world. The 2014 DBIR analyzes more than 1,300 confirmed data breaches as well as more than 63,000 reported security incidents from 94 counties. It includes 70 interesting graphs along with extensive analysis and control recommendations, and for the first time, includes security incidents that don’t result in breaches, in order to gain a better understanding of the cybersecurity landscape.
At the risk of spoiling your day, and in the hope you are sitting down, here is a brief review of some of the key findings of the 60 page report.
It begins with a top-level finding that 92 percent of the 100,000 security incidents analyzed over the past ten years can be traced to nine basic attack patterns that vary from industry to industry. These include: miscellaneous errors such as sending an email to the wrong person; crimeware (various malware aimed at gaining control of systems); insider/privilege misuse; physical theft/loss; Web app attacks; denial of service attacks; cyberespionage; point-of-sale intrusions; and payment card skimmers.
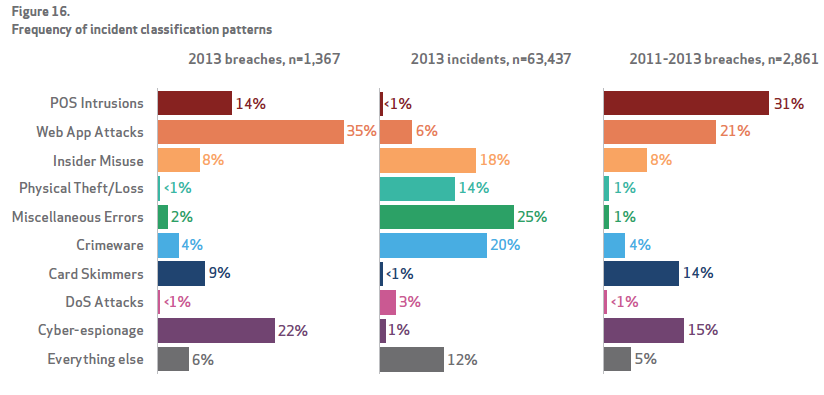
Source: Verizon 2014 Data Breach Investigations Report
This year’s report found that on average, just three threat patterns cover 72 percent of the security incidents in any industry.
Contained in the granularity of the report, for example, were the findings that in the financial services sector, 75 percent of the incidents come from Web application attacks, distributed denial of service (DDoS) and card skimming, while 54 percent of all manufacturing attacks are attributed to cyberespionage and DDoS. In the retail sector, the majority of attacks are tied to DDoS (33 percent) followed by point-of-sale intrusions (31 percent).
Other key findings by the researchers include:
- Cyberespionage is up, representing a more than three-fold increase compared with the 2013 report, with 511 incidents. (This is partially due to a bigger dataset.) In addition, attacks were found to be the most complex and diverse, with a long list of threat patterns. China still leads as the site of the most cyberespionage activity; but the other regions of the world are represented, including Eastern Europe with more than 20 percent.
- For the first time, the report examines distributed denial of service (DDoS) attacks. It found they are common to the financial services, retail, professional, information and public sector industries and have grown stronger year-over-year for the past three years.
- The use of stolen and/or misused credentials (user name/passwords) continues to be the No. 1 way to gain access to information. Two out of three breaches exploit weak or stolen passwords, making a case for strong two-factor authentication.
- Despite the headlines, retail point-of-sale (POS) attacks continue to trend downward, exhibiting the same trend since 2011. Industries commonly hit by POS intrusions are restaurants, hotels, grocery stores and other brick-and-mortar retailers, where intruders attempt to capture payment card data. That said, the researchers also comment that, “2013 may be remembered as the ‘year of the retailer breach,’ but a comprehensive assessment suggests it was a year of transition from geopolitical attacks to large-scale attacks on payment card systems.”
- While external attacks still outweigh insider attacks, insider attacks are up, especially with regard to stolen intellectual property. The report points out that 85 percent of insider and privilege-abuse attacks used the corporate LAN, and 22 percent took advantage of physical access.
“This year’s report offers unparalleled perspective into the world of cybercrime, based on big data analysis,” said Eddie Schwartz, vice president of global cybersecurity and consulting solutions at Verizon Enterprise Solutions. “The 2014 DBIR will advance how we approach cyberthreats as an industry and through our intelligence-gathering enable enterprise organizations to more strategically determine their best defense.”
Last and certainly not least, the reason this report is an absolute “must read” is that Verizon at the end of the report takes the data it has collected, and uses it to map industries to incident patterns and patterns to controls and creates a nice visualization for then mapping industries directly to recommendations for controls. I have not produced the visualizations in the hope that you will download and read the entire report.
What does pop out from a careful reading of the DBIR is that no matter which part of the security business one looks at—physical and virtual, securing people, devices, the apps on those devices, business processes and networks used, etc.— the recommendations always start with a simple but powerful call to action, i.e., get the basics right.
Whether it is protection from internal or external attacks, the numbers tend to show that making sure passwords are changed frequently, there is multi-factor authentication, software of all types whether operational or anti-malware is current, can mitigate risks and make the bad guys look elsewhere to perpetrate their mischief. No one security solution or set of them can deter determined and sophisticated cyber attacks, but given things like the patterns disclosed in the Verizon DBIR, the vectors of vulnerability are clear, even by industry, and thus inaction on shoring them up given what is at stake should not be an alternative.
The risk/reward ratio says it all, and Verizon is correct is pointing out that it is possible to bend the curve in the right direction so that when the DBIR comes out next year Baker and his colleagues do not have to say that the bad guys have increased their lead.
Edited by
Maurice Nagle