The annual Black Hat U.S. gathering of the world’s top security experts is taking place for the 17th year in Las Vegas this week. In fact, given that security is a huge component of “risk management,” it seems appropriate that Las Vegas is home to the event. It is also the place where those in the security field can get caught up on the latest activities of those with malicious intent (aka “bad guys”), and learn about best practices for thwarting attacks that are arising as a result of the expanded surfaces of attack and how to close the known weakest links in cyber-defenses.
One of the prime resources security professionals rely on to stay informed about the latest exploits of the bad guys is provided by Cisco. And, as has become something of a tradition, the company is releasing its Cisco 2014 Midyear Security Report. As has unfortunately become a tradition as well, the report (53 pages of stats and insights) is another in the rolling thunder of reports on all aspects of cyber security that details that things are not pretty out there, and organizations need to step up their game just like the bad actors continue to do so.
The Cisco 2014 Midyear Security Report examines the “weak links” in organizations that contribute to the increasingly dynamic threat landscape. These weak links – which could be outdated software, bad code, abandoned digital properties, or user errors – contribute to the adversary’s ability to exploit vulnerabilities. These vulnerabilities are not only numerous but those seeking to exploit them have lots of tools with which to work. These include methods such as DNS queries, exploit kits, amplification attacks, point-of-sale (POS) system compromise, “malvertising”, “ransomware”, infiltration of encryption protocols, social engineering and “life event” spam. In a word, “YIKES!”
One of the more interesting findings in this version of the report is its demonstration that organizations typically focus on only high-profile vulnerabilities rather than on high-impact, common and stealthy threats. This, Cisco points out, puts those organizations with that type of focus at greater risk. By proliferating attacks against low-profile legacy applications and infrastructure with known weaknesses, malicious actors are able to escape detection as security teams focus instead on headline makers such as Heartbleed.
The Report at a Glance
The context for the report, and why it is viewed as so valuable, is that Cisco researchers examined 16 large multinational organizations in their investigations. These entities as of 2013 collectively controlled over $4 trillion in assets with revenues in excess of $300 billion.
Cisco says there are three compelling security insights that are the major pullouts of the report that tie enterprises to malicious traffic:
“Man-in-the-Browser” attacks pose a risk for enterprises: Nearly 94 percent of customer networks observed in 2014 have been identified as having traffic going to websites that host malware. Specifically, issuing DNS requests for hostnames where the IP address to which the hostname resolves is reported to be associated with the distribution of Palevo, SpyEye, and Zeus malware families that incorporate man-in-the-browser (MiTB) functionality.
Botnet hide and seek: Nearly 70 percent of networks were identified as issuing DNS queries for Dynamic DNS Domains. This shows evidence of networks misused or compromised with botnets using DDNS to alter their IP address to avoid detection/blacklist. Few legitimate outbound connection attempts from enterprises would seek dynamic DNS domains apart from outbound C&C callbacks looking to disguise the location of their botnet.
Encrypting stolen data: Nearly 44 percent of customer networks observed in 2014 have been identified as issuing DNS requests for sites and domains with devices that provide encrypted channel services, used by malicious actors to cover their tracks by exfiltrating data using encrypted channels to avoid detection like VPN, SSH, SFTP, FTP, and FTPS.
Other Findings of Interest
As noted, this is a comprehensive report which is worth spending some time with. In fact, this edition includes key findings from a recent “Inside Out” project where Cisco researchers reviewed DNS lookups originating from inside corporate networks. Plus, it was developed by security research experts who are part of the Cisco Collective Security Intelligence (CSI) ecosystem which includes the newly combined Talos Threat Intelligence and Research Group.
At a high level, and probably not a surprise to anyone, Cisco found that malicious traffic was visible on 100 percent of the networks sampled. The good news is that researchers did find that the number of exploit kits has dropped by 87 percent since the alleged creator of the widely popular “Blackhole” exploit kit was arrested last year. The not good news is that the market hates a vacuum and new exploit kits are mushrooming with a clear leader yet to emerge.
Other items of note included the fact that Java remains the most exploited programming language for attack at 93 percent. Adobe Reader, Microsoft Word, Microsoft PowerPoint and Excel make up the remaining seven percent. The trend is in line with previous reports, and a clear warning to IT professionals to get rid of older versions of Java for one thing, and to pay extra attention to newer versions as well.
The graphic below is also food for thought and consternation. It highlights what Cisco rightly calls “unusual upticks in malware within vertical markets.”
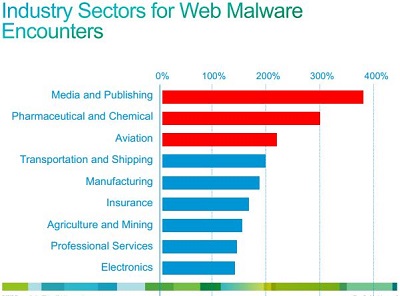
Source: Cisco 2014 Midyear Security Report
As the report explains, for the first half of 2014, the pharmaceutical and chemical industry, a high-profit vertical, once again placed in the top three high-risk verticals for Web malware encounters. Media and publishing surprisingly led the industry verticals, posting nearly four times the median Web malware encounters, and aviation slid into third place with over twice the median Web malware encounters globally.
Commenting on the findings, John N. Stewart, senior vice president and chief security officer at Cisco said, “Many companies are innovating their future using the Internet. To succeed in this rapidly emerging environment, executive leadership needs to embrace and manage, in business terms, the associated cyber risks. Analyzing and understanding weaknesses within the security chain rests largely upon the ability of individual organizations, and industry, to create awareness about cyber risk at the most senior levels, including Boards — making cyber security a business process, not about technology. To cover the entire attack continuum — before, during, and after an attack—organizations today must operate security solutions that operate everywhere a threat can manifest itself.”
I did have a chance to speak with report author Cisco TRAC lead security analyst Levi Gundert about the report. He noted not just the drop in exploit kits, but also said other good news is that point-of-sale (POS) attacks, which are common in the U.S. due to lack of chips and stronger authentication used in the rest of the world, which were highlighted by the Target hack, “should become obsolete.”
Gundert did educate me on something that the U.S. Senate released a recent report about, malvertising. If you are not familiar with the term, you soon will be. As Gundert explained, “This is a huge problem that is much larger than consumers and businesses understand. In fact, already 5-10 percent of the blocked URLs we are seeing are related to malvertising. It is really insidious.”
He walked me through why. It is actually ingenious as well as insidious. Bad guys need to push their victims to an exploit kit landing page. They do so by injecting malware into advertising. This advertising tends to be distributed on the Web via advertising exchanges which to be polite are less than diligent about the integrity of the ads they are pushing. What this means is that if you or I visit Web page XYZ, if a malware-infected ad is on that page we don’t even have to open the ad to be captured. As Gundert noted, this is a huge and growing problem that needs to be addressed with some sense of urgency because it compromises the trust we all have in visiting popular websites that have lots of ads like CNN, ESPN, etc.
As they say in Las Vegas, “you roll the dice and you take your chances.” What the Cisco 2014 Midyear Security Report highlights is that there are significant steps you can take to cut your losses, and shoring up those weakest links are where organizations need to start.
Edited by
Rory J. Thompson