The question of the day, as enterprise around the world increasingly design their products and applications for personal devices in the “Mobile First” strategy, is as follows: Is enough attention and resource being paid to securing mobile apps?
The answer according to a new study, The State of Mobile Application Insecurity, by the Ponemon Institute for IBM Security is a resounding “no!” In fact, if you read the entire 31 page study, which I can’t recommend highly enough, the real answer that comes to mind is “hell no!” The emphasis being as much on the hell as the no since the consequences of not securing mobile apps properly in a mobility-centric world can be catastrophic.
At a high level the findings are alarming to say the least. They show that nearly 40 percent of large companies, including many in the Fortune 500, aren’t taking the right precautions to secure the mobile apps they build for customers. The study also found organizations are poorly protecting their corporate and BYOD mobile devices against cyber-attacks. As we all know from reading the almost daily reports of another cyberattack, as the vectors of vulnerability increase, it only takes one open door, be it internal as brought in by a BYOD device or via an external assault for hackers to compromise individual user data and more importantly, look around for the big fish they can fry.
Shocking!
Every security study in the past few months has highlighted that 2014 was a very good year for the bad guys. They add that 2015 looks even better. It is estimated that malicious code is infecting more than 11.6 million mobile devices. In addition, according to IBM X-Force research, in 2014 alone, over 1 billion pieces of personally identifiable information (PII) were compromised as a result of cyber-attacks.
The Ponemon Institute and IBM Security study, which researched security practices in over 400 large organizations, found disturbingly that:
- The average company tests 40 percent of the mobile apps they build
- 33 percent of companies never test their apps
- 50 percent of these organizations were found to devote zero budget whatsoever towards mobile security.
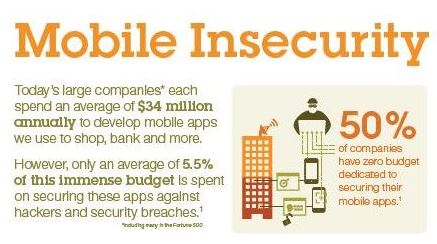 Source: IBM
Source: IBM
An infographic supplied by IBM with the release of the report provides context. After all one could conclude that 5.5 percent of a big number is a big number and $34 million seems like a lot of money.
 Source: IBM
Source: IBM
“Building security into mobile apps is not top of mind for companies, giving hackers the opportunity to easily reverse engineer apps, jailbreak mobile devices and tap into confidential data,” said Caleb Barlow, Vice President of Mobile Management and Security at IBM. “Industries need to think about security at the same level on which highly efficient, collaborative cyber criminals are planning attacks. To help companies adopt smart mobile strategies, we've tapped the deep security expertise of IBM Security Trusteer, bringing what we've learned from protecting the most sensitive data of complex organizations - such as top global banks - and applying it to mobile.”
But wait, there is more
The reason to spend quality time with this study is the depth of detail contained. The information revolves around Ponemon’s organization of the results around the following themes:
- Why mobile application security eludes many organizations.
- The difficulty in controlling employees’ risky behaviors.
- Are organizations taking the right steps to secure mobile apps?
This is a page-turner and just a few of the findings show why. For example, during the creation of mobile apps, end user convenience is trumping end user security and privacy. According to the study, 65 percent of organizations state the security of their apps is often put at risk because of customer demand or need, and 77 percent cite “rush to release” pressures as a primary reason why mobile apps contain vulnerable code. This rush results in only 15 percent of respondents saying they test their apps as frequently as needed to be effective.
Another tidbit that is food for thought is seen in the graphic from the report shown below.
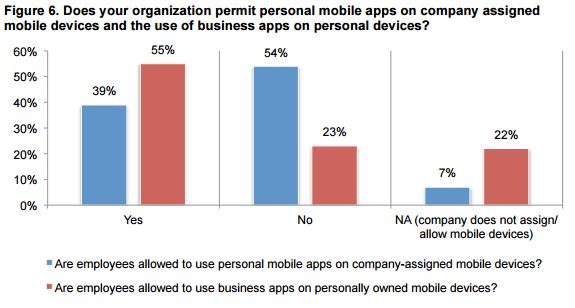 Source: IBM
Source: IBM
It is hard to draw any conclusion from the above graphic other than the door has been left wide open. As discussed in the commentary on the findings, the challenge of securing the mobile enterprise is complex. Employees connect to unsecured networks or download insecure apps from untrusted sources. Worse, as uncovered by the Ponemon Institute’s findings, even apps from trusted organizations available in traditional app stores can carry enormous risks.
A recommended solution
Having sounded the alarm, IBM is using the report as a vehicle to promote a solution to the issues raised by it. IBM has introduced a new mobile threat management (MTM) technology into its IBM MobileFirst Protect offering (formerly MaaS360). The solution automatically detects suspicious activities on mobile endpoints, and stops malware the moment a device is breached. In fact, the solution is illustrative of another growing industry trend where the once thought insecure cloud is used to deliver security. This is precisely what IBM is doing and it provides devices updated security over-the-air. The advantage is the high probability of stopping attacks at their source before they can spread.
As IBM says, “Built by IBM Security, the offering’s new threat management technology integrates the flexible power of cloud, the comprehensive control of enterprise mobility management, and the most sophisticated defense tools yet created against malware and mobile fraud.” And, the good news is you can try IBM MobileFirst Protect Threat Management for free.
The report is obviously a call to action for IT security professionals and C-levels to invest more in mobile threat management. It also should be something that app developers understand when they are creating their apps, i.e., security matters from creation to cash to deployment and operation.
Edited by
Dominick Sorrentino