The distributed nature of work is an immutable trend. It is only picking up steam thanks to mobility, the cloud and multinational enterprises practicing the advice taught in MBA programs around the world to “think globally but act locally.”
This continued distributed nature of work is increasing pressure on IT professionals to have greater visibility and management of their entire “E”vironments. In particular, knowing a lot more about what is going on in the network segments that connect various locations along with internal traffic has become critical. As the headlines shout every day, there is a growing urgency for IT to have real-time, visibility into network traffic. Plus they also need granularity/context so they can not only just identify but track suspicious behaviors that can enable or obscure network attacks.
Vectra Networks, an innovator in solutions that enable IT to detect cyber attacks in real-time while they are in progress, has announced new capabilities that can provide the good guys the expanded visibility they desire and the bad guys something to think about. They have introduced:
- The S-series sensor: an extension to the company’s threat detection platform of its automated real-time, cybersecurity into all corners of an organization. This includes previous blind spots such as remote sites and internal network segments.
- Detection Triage functionality: enabling security teams to identify and track risky behaviors so as to proactively and not just reactively prevent bad things very early.
As Mike Banic, Vectra vice president of marketing told TechZone360, “The weak links in an expanding attack surface are remote sites. Historically securing them has been too expensive. Plus, as the perimeter of the network, there has not been visibility into the core”. He added that as recent attacks have demonstrated, “There is a need to monitor east-west as well as north-south. IT needs a broader view of what is going on internally via continuous monitoring and we also believe they need prioritized contextual results so as our new Detection Triage capability does, you can literally make decisions about what critical anomalies to address and when.”
What Banic highlighted is that the history of cybersecurity defenses has been to look for attacks only at the organization’s Internet boundary and main sites. Unfortunately, sophisticated hackers know to attack the weakest links, i.e., remote sites. These areas often lack the visibility to detect the subtle signs of an attacker spying, spreading and stealing within the network. Once inside, as the recent Premera and other attacks have illustrated, attackers take their time to look around before really wreaking havoc.
According to Forrester Research, “Many security and risk pros are not even aware when the enterprise has already suffered a breach. This is commonly caused by underinvestment in network analysis and visibility (NAV) and endpoint visibility and control (EVC) tools that can detect abnormal patterns and user behavior in their networks and IT environment.”1
Where does advanced detection fit?
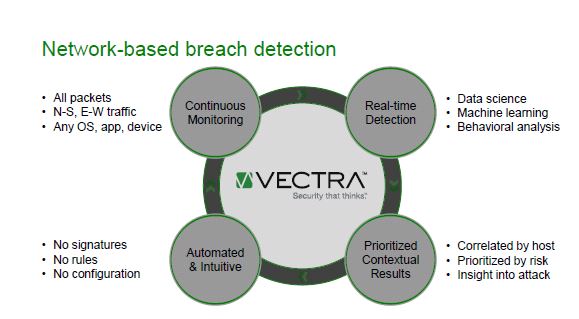
In answering the question of where the new sensors and triage capabilities fit, a view of Vectra Network’s approach to network-based breaches is helpful.
 Source: Vectra Networks
Source: Vectra Networks
The S-Series is in the continuous monitoring part of the vision as it looks at traffic while the Detection Triage occupies the prioritized contextual results area.
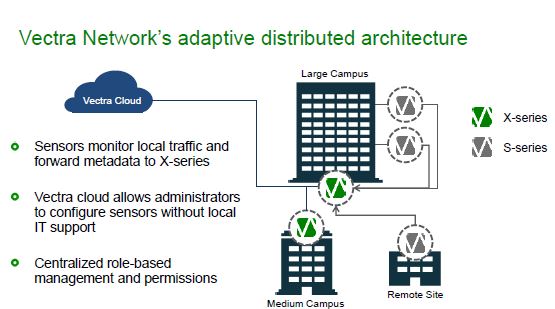
As the schematic below illustrates, the S-Series sensors are located at remote sites. They are passive devices; hence do not add latency to communications. They also have small footprints and low power consumption, and work as vital end points in Vectra’s overall network performance monitoring solutions approach.
Vectra has packed a lot of punch into the sensors including:
- They are less costly than larger sensors (list price of $8,000) making the affordable for remote site deployment.
- Have over twice the throughput of other sensors and thus can handle looking at the expanding traffic at remote sites.
- Deliver “full fidelity” security
- Working in as part of a Vectra X-series holistic monitoring solution they can cover up to 20 remote sites at significantly reduced cost.
- Provide reporting in a single pane view.
 Source: Vectra Networks
Source: Vectra Networks
“Vectra is the first to extend real-time cybersecurity to remote sites and internal segments to automate detection of all phases of an attack anywhere in an organization,” said Hitesh Sheth, Vectra CEO. “Combining sensors with our X-series platform allows our customers to automatically see indicators of a cyber attack anywhere in the network without incremental investment in system analyst resources.”
The new Vectra Detection Triage capability should not be overlooked. Current solutions can not see or can be blinded to attacker reconnaissance, for example. It is why having the ability to customize and track detections of anomalous behaviors using local context is so important to early cyber attack detection so remediation can be quickly put in place.
This is another popular saying that is very applicable, “knowledge is power.”
There is no denying that for obvious reasons those with malicious intent are going to continuously look for the weakest link to gain access to an enterprise’s digital assets. As cyber security experts have been saying for several years, the barbarians are not at the gate—they have gone around it. This is why having visibility of all traffic, regardless of direction or location, is now a matter of necessity for enabling IT to better manage risks.
This is why shoring up visibility of remote sites should be a priority, as the consequences of not doing so are demonstrated constantly. It is also why watching that east-west traffic is so important, and why local contextual real-time information that scores risk potential are becoming critical as well. After all, if your organization is under a persistent attack, hopefully it does not take you months to even discover the fact. Knowing sooner rather than later so IT can be proactive as well as more responsive is why so much attention is being paid to solutions that provide deep real-time visibility into every aspect of networking, and why watching data on the move on these networks has such a high value for good guys and bad guys alike.
Note1: Forrester Research, “Planning for Failure,” by John Kindervag, Rick Holland and Heidi Shey, Feb. 11, 2015.