Kaspersky Lab is a major, privately held security vendor that has teamed with IT security experts now for the better part of 15 years. Kaspersky is a key vendor in the delivery of endpoint protection solutions, and the company targets both large businesses as well as SMBs. It currently operates in close to 200 countries, providing protection for over 300 million users. From this vantage point, the company has now pieced together what it believes will be the key security threats enterprises and tech users can expect to encounter in 2013. When Kaspersky speaks on enterprise IT security we find that it’s usually well worth listening to what it has to say.
The most notable predictions for the next year include the continued rise of targeted attacks, cyber-espionage and nation-state cyber-attacks, the evolving role of “hacktivism,” the development of controversial and supposedly legal surveillance tools and the increase in cybercriminal attacks targeting cloud-based services.
Before we get into their 2013 predictions, let’s take a quick look at how the company believes 2012 – which it has dubbed the explosive year of malware growth - panned out from the point of view of the top 10 security events for the year (if you just can’t wait, scroll right down to the 2013 predictions, but the 2012 events are well worth the preamble to 2013):
- Flashback hits Mac OS X: Although the Mac OS X Trojan Flashback/Flashfake appeared in late 2011, it wasn’t until April 2012 that it became really popular, with an estimated 700,000 Macs infected - easily the biggest known MacOS X infection to date. Flashback is especially relevant because it demolished the myth of security invulnerability surrounding the Mac.
- Flame and Gauss: Nation-state Cyber-espionage Campaigns: In mid-April 2012, a series of cyber-attacks destroyed computer systems at several oil platforms in the Middle East. The malware responsible for the attacks, named “Wiper”, was never found – although several pointers indicated a resemblance to Duqu and Stuxnet. During the investigation, Kaspersky came across a huge “cyber-espionage campaign” now known as Flame - one of the most sophisticated pieces of malware ever created, with the ability to infect fully patched Windows 7 PCs at the blink of an eye. The complexity of this operation left no doubt that this was backed by a nation-state. Flame was followed by Gauss, another highly sophisticated Trojan that was widely deployed in the Middle East, added a new dimension to nation-state cyber campaigns. Some pieces of Gauss remain a mystery to this day.
- The Explosion of Android Threats: Perhaps more mundane sounding, but never the less huge, Kaspersky found an explosion in the number of malicious threats targeting the Android platform. The chart below shows exactly hoe explosive it’s been:
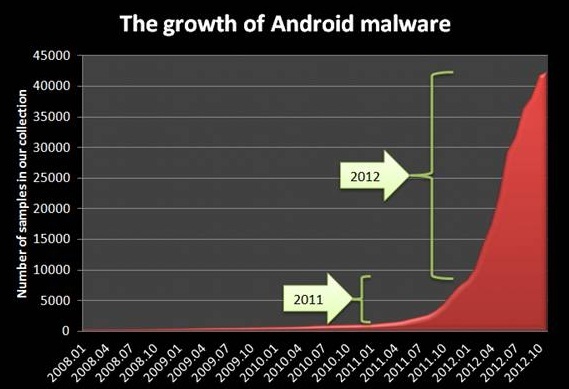
- The LinkedIn, Last.fm, Dropbox and Gamigo Password Leaks: On 5 June 2012, LinkedIn was hacked by unknown assailants and the password hashes of more than 6.4 million people leaked onto the Internet. Then DropBox announced that it was hacked and user account details were leaked (one of the major issues enterprises have with such cloud-based primarily consumer tools). This was followed by Last.fm and Gamigo intrusions, where more than eight million passwords were leaked to the public. These attacks show that in the age of the “cloud” when information about millions of accounts is available in one server, over speedy Internet links, the concept of data leaks takes on extraordinary new dimensions.
- The Adobe Certificates Theft and the Omnipresent APT: On September 27, 2012, Adobe announced the discovery of two malicious programs that were signed using a valid Adobe code signing certificate. Adobe’s certificates were securely stored in an HSM, a special cryptographic device which makes attacks much more complicated. Nevertheless, the attackers were able to compromise a server that was able to perform code signing requests. The fact that a high profile company like Adobe was compromised in this way redefines the boundaries and possibilities that are becoming available for these high-level attackers. YOU should be worried!
- The DNSChanger Shutdown: When the culprits behind the DNSChanger malware were arrested in November 2011 during the “Ghost Click” operation, the identity-theft infrastructure was taken over by the FBI. Very interestingly, the FBI then agreed to keep the servers online until 9 July 2012, so the victims could have time to disinfect their systems. It was a large scale action that showed that success against cybercrime can be achieved through open cooperation and information sharing.
- The Ma(h)di Incident: During late 2011 and the first half of 2012, an ongoing campaign to infiltrate computer systems throughout the Middle East targeted individuals across Iran, Israel, Afghanistan and others scattered across the globe, which Kaspersky named “Madi”, based on certain strings and handles used by the attackers. Madi was fairly unsophisticated, but it succeeded in compromising many different victims around the globe through social engineering and Right-To-Left-Override tactics.
- The Java 0-days: In the aftermath of the previously mentioned Flashback incident, Apple took a bold step and decided to disable Java across millions of Mac OS X users. But August 2012, a Java zero-day vulnerability was found to be massively used in-the-wild. The exploit was implemented in the wildly popular BlackHole exploit kit and quickly became responsible for millions of infections worldwide. During the second quarter of 2012, Kaspersky performed an analysis of vulnerable software found on users’ computers and found that more than 30 percent of them still had an old and the most vulnerable version of Java installed!
- Shamoon: In the middle of August, details appeared about a piece of highly destructive malware that was used in an attack against Saudi Aramco, one of the world’s largest oil conglomerates. According to reports, more than 30,000 computers were completely destroyed by the malware. Shamoon is important because it brought up the idea used in the Wiper malware, which is a destructive payload with the purpose of massively compromising a company’s operations. As in the case of Wiper, many details are still unknown.
- DSL Modem Hardware Hacks: In October 2012, Kaspersky researcher Fabio Assolini published the details of an attack which had been taking place in Brazil since 2011 using a single firmware vulnerability, two malicious scripts and 40 malicious DNS servers. This operation affected six hardware manufacturers, resulting in millions of Brazilian Internet users falling victim to a sustained and silent mass attack on DSL modems. In March 2012, Brazil’s CERT team confirmed that more than 4.5 million modems were compromised in the attack and were being abused by cybercriminals for all sorts of fraudulent activity. The DSL router issues in Brazil are not random incidents - they are clear indications that hardware routers can pose the same if not higher security risks as older or obscure software that is never updated.
Key Security Predictions for 2013
The future is always rooted in the present, hence the preamble above outlining the key trends of 2012 – which we believe offers a good starting point to looking ahead to 2013. Costin Raiu, Kaspersky’s director of global research & analysis team, puts it this way: “In our previous reports we categorized 2011 as the year of explosive growth of new cyber threats. The most notable incidents of 2012 have been revealing and shaping the future of cyber security. We expect the next year to be packed with high-profile attacks on consumers, businesses and governments alike, and to see the first signs of notable attacks against the critical industrial infrastructure. The most notable trends of 2013 will be new example of cyber warfare operations, increasing targeted attacks on businesses and new, sophisticated mobile threats.”
So then, for 2013:
- Targeted Attacks and Cyber-espionage: While the threat landscape is still dominated by random, speculative attacks, “targeted attacks” have become an established feature in the last two years. Such attacks are specifically tailored to penetrate a particular organization and are often focused on gathering sensitive data that has a monetary value. Targeted attacks can often be highly sophisticated, but many attacks start by simply “hacking the human” and tricking employees into disclosing information that can be used to gain access to corporate resources. Kaspersky expects the growth of cyber-espionage to continue into 2013 and beyond. Mobility and BYOD add substantially to the threats.
- The Onward March of Hacktivism: Sometimes the purpose of an attack is to make a political or social point. There was a steady stream of such attacks in 2012. This includes, for example, attacks launched by Anonymous on government websites in Poland, following the government’s announcement that it would support ACTA (the Anti-Counterfeiting Trade Agreement). Society’s increasing reliance on the Internet makes organizations of all kinds potentially vulnerable to attacks of this sort, so look for hacktivism to continue into 2013 and beyond.
- Nation-state-sponsored Cyber-attacks: Stuxnet pioneered the use of highly sophisticated malware for targeted attacks on key production facilities. We are now entering a new Stuxnet-like “cold cyber-war” era. Expect more countries to aggressively develop cyber weapons in 2013 – designed to steal information or sabotage systems. We’ll likely also see “copy-cat” attacks by non-nation-states, with an increased risk of collateral damage beyond the intended victims of the attack. The targets for such cyber-attacks could include energy supply and transportation control facilities, financial and telecommunications systems and other ‘critical infrastructure’ facilities.
- The Use of Legal Surveillance Tools: Cybercrime has become more and more sophisticated and creates new challenges for anti-malware researchers, but also for law enforcement agencies around the world. Their efforts to keep pace with the advanced technologies being used by cybercriminals are driving them in directions that have obvious implications for law enforcement itself. This includes, for example, what to do about compromised computers after the authorities have successfully taken down a botnet. It also includes using technology to monitor the activities of those “suspected” of criminal activities. Clearly, the use of legal surveillance tools has wider implications for privacy and civil liberties. And as law enforcement agencies, and governments, try to get one step ahead of the criminals, it’s likely that the use of such tools – and the debate surrounding their use – will continue.
- Cloudy with a Chance of Malware: In the world of clouds, it's crystal clear that the use of cloud services will grow enormously in 2013 and well beyond. But as the use of the cloud grows, so too will the number of security threats that target it. First, the data centers of cloud providers form an attractive target for cybercriminals. Looked at from the perspective of a cybercriminal, clouds offer a potential single-point-of-failure, along with monster quantities of personal data in one place that can be stolen in one fell swoop if the provider should fall victim to a successful attack. Second, cybercriminals are likely to make more use of cloud services to host and spread their malware – typically through stolen accounts. Third, data stored in the cloud is accessed from real devices that cybercriminals can easily compromise. The wide use of mobile devices as access points into the cloud must remain a top priority for enterprises.
- Dude, Where’s my Privacy: The erosion, or loss, of privacy - especially as mobility grows - has become a hotly-debated issue in IT security. The Internet pervades our lives and many people routinely bank, shop and socialize online. The value of personal data – to cybercriminals and legitimate businesses – will only grow in the future, and with it the potential threat to our privacy increases enormously and must be protected at all costs.
- Who do You Trust: We’re all predisposed to trust websites with a security certificate issued by a bona fide Certificate Authority (CA), or an application with a valid digital certificate. Unfortunately, not only have cybercriminals been able to issue fake certificates for their malware – using so-called self-signed certificates – they have also been able to successfully breach the systems of various CAs and use stolen certificates to sign their code. The use of fake, and stolen, certificates is set to continue in the future. But the problem may well be compounded by a further development. In recent years, white listing has been added to the arsenal of security vendors – that is, checking code not only to see if it’s known to be malicious, but also checking to see if it’s “known-good.” But rogue applications can find their way onto a white list, where they could then safely fly under the radar of security programs and go undetected. This is going to be a major issue in 2013 and enterprises must ensure there are no such under the radar vulnerabilities.
- Cyber Extortion: Ransomware trojans (also the topic of Neil Stephenson’s recent novel, Reamde) are specifically designed to extort money from their victims, either by encrypting data on a user’s disk or by blocking access to a system, and they have become disturbingly frequent. Until fairly recently this type of cybercrime was confined largely to Russia and other former Soviet countries. Such attacks are easy to develop and, as with phishing attacks, there seem to be no shortage of potential victims. As a result, Kaspersky believes we are likely to see their continued growth in the future.
- Mac OS Malware: Despite well-entrenched perceptions, Macs are not immune to malware. Of course, when compared with the torrent of malware targeting Windows, the volume of Mac-based malware is small. However, it has been growing steadily over the last two years and it would be naïve and foolish of anyone using a Mac to believe they are protected for becoming victims of cybercrime. It’s not only generalized attacks – such as the 700,000-strong Flashfake botnet from earlier this year that pose a threat. There are now targeted attacks on specific groups, or individuals specifically known to use Macs. The threat to Macs is real and will grow.
- Mobile Malware: Mobile malware is an almost redundant set of words today, and it has exploded in the last 18 months. The lion’s share of it continues to target Android-based devices and most such malware is designed to gain access to devices. In the future we are likely to see the use of vulnerabilities that target the operating system and based on this the development of what is now referred to as “drive-by downloads.” There is also a high probability that the first mass worm for Android will appear, capable of spreading itself via text messages and sending out links to itself at some online app store. We’re also likely to see more mobile botnets, of the sort created using the RootSmart backdoor in early 2012. By contrast, iOS is a closed, restricted file system, allowing the download and use of apps from just a single source, the App Store. This means a much lower security risk, though the appearance of the ‘Find and Call’ app earlier this year has shown that it’s possible for undesirable apps to slip through Apple’s protective net as well. Regardless, Android will remain the chief focus of cybercriminals in 2013.
- Vulnerabilities and Exploits: The key method most used by cybercriminals to install malware on victims’ computers is to simply exploit un-patched vulnerabilities in applications. Java vulnerabilities currently account for more than 50 per cent of attacks, while Adobe Reader accounts for a further 25 percent. Cybercriminals will continue to exploit Java in the year ahead. Always ensure you have the latest version of Java – don’t skimp on updates – do the installs! It’s likely that Adobe Reader will also continue to be used by cybercriminals, but probably less so because the latest versions provide an automatic update mechanism.
It’s not a safe cyber world out there, and though being forewarned provides a measure of being forearmed, it will take a huge amount of vigilance on the part of enterprises to keep their businesses secure. Don’t trust your users to cover for your business. They won’t – it’s simply human nature. Enforcement must come from the enterprise side, and enterprises must make sure – especially relative to BYOD-driven mobility – that they urgently do so.
Edited by
Brooke Neuman