Augmented Reality Gets an Upgrade as Result of New Partnership Between Lumus and AddOptics
Lumus and AddOptics - the former an AR optics company developing reflective wavelength tech, the latter an AR lens/smart-wear prescription provider - …
Read MoreThe Rise of Eco-Apps: Hear How Technology is Helping Us Live Greener Lives
In recent years, technology has revolutionized how we approach sustainability. One of the most significant developments in this realm is the advent of…
Read MoreIntroducing the Newest Addition to ITEXPO #TECHSUPERSHOW: Enterprise Cybersecurity Expo
TMC today announced the launch of Enterprise Cybersecurity Expo, set to take place from February 11-13, 2025, in Fort Lauderdale, Florida, at the Brow…
Read MoreThe Shifting Landscape: Emergent Technological Paradigms in Online Sports Wagering
In the ever-evolving sphere of online sports wagering, technological advancements have been instrumental in reshaping the landscape, altering how enth…
Read MoreUnpacking The Differences: How CPaaS And Network APIs Drive Distinct Innovations
While they share some technical synergies, CPaaS and Network APIs serve different markets and purposes, highlighting the need for complementary strate…
Read MoreProtecting Your Digital Fortress Through Threat Exposure Management
In today's digital landscape, cybersecurity threats loom large, posing significant risks to businesses, organizations, and individuals alike. With the…
Read MoreWhy Block Websites? Understanding the Reasons
The internet is such an expansive network where every click can lead to information, entertainment, or opportunities for productivity. However, this a…
Read MoreChatGPT Isn't Really AI: Here's Why
ChatGPT is the biggest talking point in the world of AI, but is it actually artificial intelligence? Click here to find out the truth behind ChatGPT.
Read MoreRevolutionizing Home Energy Management: The Partnership of Hub Controls and Four Square/TRE
Through a recently announced partnership with manufacturer Four Square/TRE, Hub Controls is set to redefine the landscape of home energy management in…
Read More4 Benefits of Time Tracking Software for Small Businesses
Time tracking is invaluable for every business's success. It ensures teams and time are well managed. While you can do manual time tracking, it's time…
Read MoreHow the Terraform Registry Helps DevOps Teams Increase Efficiency
A key component to HashiCorp's Terraform infrastructure-as-code (IaC) ecosystem, the Terraform Registry made it to the news in late 2023 when changes …
Read MoreNightmares, No More: New CanineAlert Device for Service Dogs Helps Reduce PTSD for Owners, Particularly Veterans
Canine Companions, a nonprofit organization that transforms the lives of veterans (and others) suffering PTSD with vigilant service dogs, has debuted …
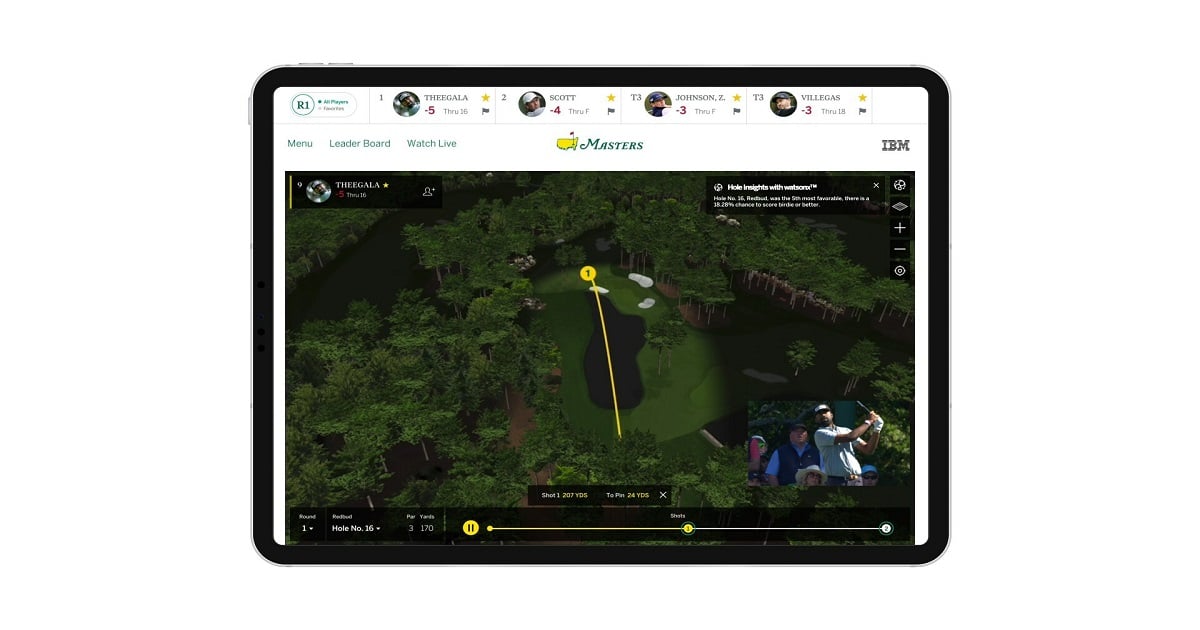
Read MoreIBM's AI Brings Data-Driven Insights and Spanish Narration to the Masters
The Masters Tournament and IBM announced new features for the 2024 Masters app and Masters.com, powered by watsonX.
Read MoreInnovating Organic Waste Management: John Gessin Explores Technological Advances in Green Waste Recovery
In recent years, there has been a growing awareness about the negative impact of traditional waste disposal methods on our environment. As a result, i…
Read MoreIceotope Reinforces Industry Leadership to Make the Most of Precision Liquid Cooling Solutions
Earlier today, Iceotope announced that it is officially welcoming Christian Belady as its new Senior Advisor. Moreover a new U.S. headquarters has bee…
Read MoreUnderstanding Cybersecurity Risks in Cryptocurrency Investments
There are many unique opportunities for investment in the cryptocurrency and blockchain industry. With several thousand different digital assets and a…
Read MoreCan Science Outsmart Deepfake Deceivers? Klick Labs Proposes an Emerging Solution
Researchers at Klick Labs were able to identify audio deepfakes from authentic audio recordings via new vocal biomarker technology (alongside AI model…
Read MoreTop 5 Best Ways to Integrate Technology for Successful Project-Based Learning
Project-based learning, also popularly known as the PBL curriculum, emphasizes using and integrating technology with classroom teaching. This approach…
Read MoreHow to Protect Your Website From LDAP Injection Attacks
Prevent LDAP injection attacks with regular testing, limiting access privileges, sanitizing user input, and applying the proper encoding functions.
Read MoreAzure Cost Optimization: 5 Things You Can Do to Save on Azure
Azure cost optimization is the process of managing and reducing the overall cost of using Azure. It involves understanding the resources you're using,…
Read MoreMassive Meta Apps and Services Outage Impacts Users Worldwide
Meta's suite of apps and services are experiencing major global outages on Super Tuesday 2024.
Read MoreThe Role of Technology in Shaping the Future of Affiliate Marketing
In the current rapidly growing digital world, affiliate marketing is still one of the most effective ways for businesses to increase their visibility …
Read MoreThe Steps You Can Take To Improve Customer Service For Your Business
When you're in a competitive market, providing exceptional customer service is crucial for the success and growth of your business. Good customer serv…
Read MoreDigital Efficiency: How Today's Technology Is Shaping Tomorrow's Workflows
Digital efficiency is fast becoming the cornerstone of business operations, reshaping workflows with an unprecedented pace and precision. As companies…
Read MoreHubControls: Pioneering Energy Justice with Smart Savings and Inclusive Technologies
The HubBrain is a solution that currently provides average savings of 33% to its 12,000 users with installments working concurrently across Europe, Bi…
Read MoreProduct Feed Management: What are the Best Strategies for E-commerce Success?
In the dynamic world of e-commerce, the efficiency and effectiveness with which a company manages its online presence can be a critical factor in its …
Read MoreWeb3 in 2024 - What's the Story So Far?
Is Web3 a thing yet? Click here to learn about the 2024 Web3 story so far.
Read MoreShabodi Accelerates Adoption of Network-Aware Applications with CAMARA API Enterprise Reference Implementation
Shabodi, an Application Enablement Platform (AEP) provider unleashing advanced network capabilities in LTE, 5G, 6G, and Wi-Fi 6, announced they have l…
Read MoreHow Much Does Endpoint Protection Cost? Comparing 3 Popular Solutions
Endpoint protection, also known as endpoint security, is a cybersecurity approach focused on defending computers, mobile devices, servers, and other e…
Read MoreWhat Is Databricks? Simplifying Your Data Transformation
Databricks is an innovative data analytics platform designed to simplify the process of building big data and artificial intelligence (AI) solutions. …
Read MoreWhat Is Blue/Green deployment?
Blue/green deployment is a software release management strategy that aims to reduce downtime and risk by running two identical production environments…
Read MoreThe Threat of Lateral Movement and 5 Ways to Prevent It
Lateral movement is a term used in cybersecurity to describe the techniques that cyber attackers use to progressively move through a network in search…
Read MoreKalibr8 Ushers in a New Era of Cloud Management with Singularity for Azure
Singularity positions itself to reduce friction and streamline a number of processes, allowing organizations to cut down on unmanageable resources and…
Read MoreSecuring $30M for Device and Hardware Manufacturer Support, Xyte Continues its Future-Forward Journey
Earlier today, Xyte announced the success of its new investment round - $30 million in total funding was raised from Intel Capital, Samsung Next, and …
Read MoreWhat Is OpenTelemetry?
OpenTelemetry is an open-source project within the Cloud Native Computing Foundation (CNCF) that aims to provide a unified set of APIs, libraries, age…
Read MoreCodemantra Introduces Calabrai, a New Brand For Their CX-One SaaS IDP Platform
Codemantra unveiled its new brand, Calibrai, focused on driving software-powered innovation and automation, addressing the content transformation need…
Read MoreStrategies for a Smooth Tech Business Acquisition
A tech business acquisition is a huge feat, whether you acquire a company or one takes over yours. This can be an exciting time for both organizations…
Read More7 Innovative Ways Technology is Revolutionizing Product Testing
Product testing is a crucial component of development. Companies want to ensure high quality items that last. However, as technology advances, so do t…
Read MoreIs Commercial Printing Out of Style?
Once upon a time, commercial printing was a necessity if you wanted to reach new customers. However, as more and more people got online and the scope …
Read MoreTechnological Tools For Enhancing Post-College Job Placement: Leveraging Linkedin, Job Boards, And Virtual Career Fairs
Recent graduates face the challenge of standing out in a crowd of qualified candidates. Fortunately, with the advent of technology, powerful tools are…
Read MoreWhat Is Software Mapping?
Software mapping is the practice of diagramming and visualizing the intricacies and dependencies within a software system. It gives a bird's eye view …
Read MoreWhat Is Attribute Based Access Control?
Attribute-Based Access Control (ABAC) represents a paradigm shift in managing access rights within complex and dynamic IT environments. Unlike traditi…
Read MoreRaising Value: The Strategic Gains of Embracing Bundled Result
Where the concept of value is not just a price tag but a carefully crafted now. In a world brimming with options, the art of planned bundling has aris…
Read MoreTech Innovation in iGaming
iGaming is one of the fastest growing industries on the internet. For those who may not be aware, iGaming refers to online casinos, online slots, poke…
Read More8 Underrated Features of Your Mobile Device You Probably Didn't Know About
It is easy to get lost in all the new phone releases when multiple happen yearly. Consequently, most new functions go unnoticed because people do not …
Read MoreNavigating the Launch: A Step-by-Step Guide to Bringing Your Product to Market
Embarking on the journey to bring a new product into the marketplace is an exhilarating adventure that blends the thrill of innovation with the meticu…
Read MoreRunning MySQL on AWS: Step by Step
MySQL on AWS is the deployment of the MySQL database system on Amazon Web Services (AWS) cloud platform. MySQL is one of the most popular open-source …
Read More4 Easy Responsive Image Techniques
Responsive images are a fundamental component in responsive web design. They adapt to the size of the user's screen, delivering the best user experien…
Read More5 Types of Documentation Tools and How to Choose
Documentation tools are specialized software applications designed to help you create, manage, and publish digital documents. These tools are essentia…
Read MoreThe Intersection of Ethics And Corporate Governance: Building Trust In Business
Corporate governance is a crucial aspect of running a successful business. It encompasses the processes, practices, and policies that guide how a comp…
Read More